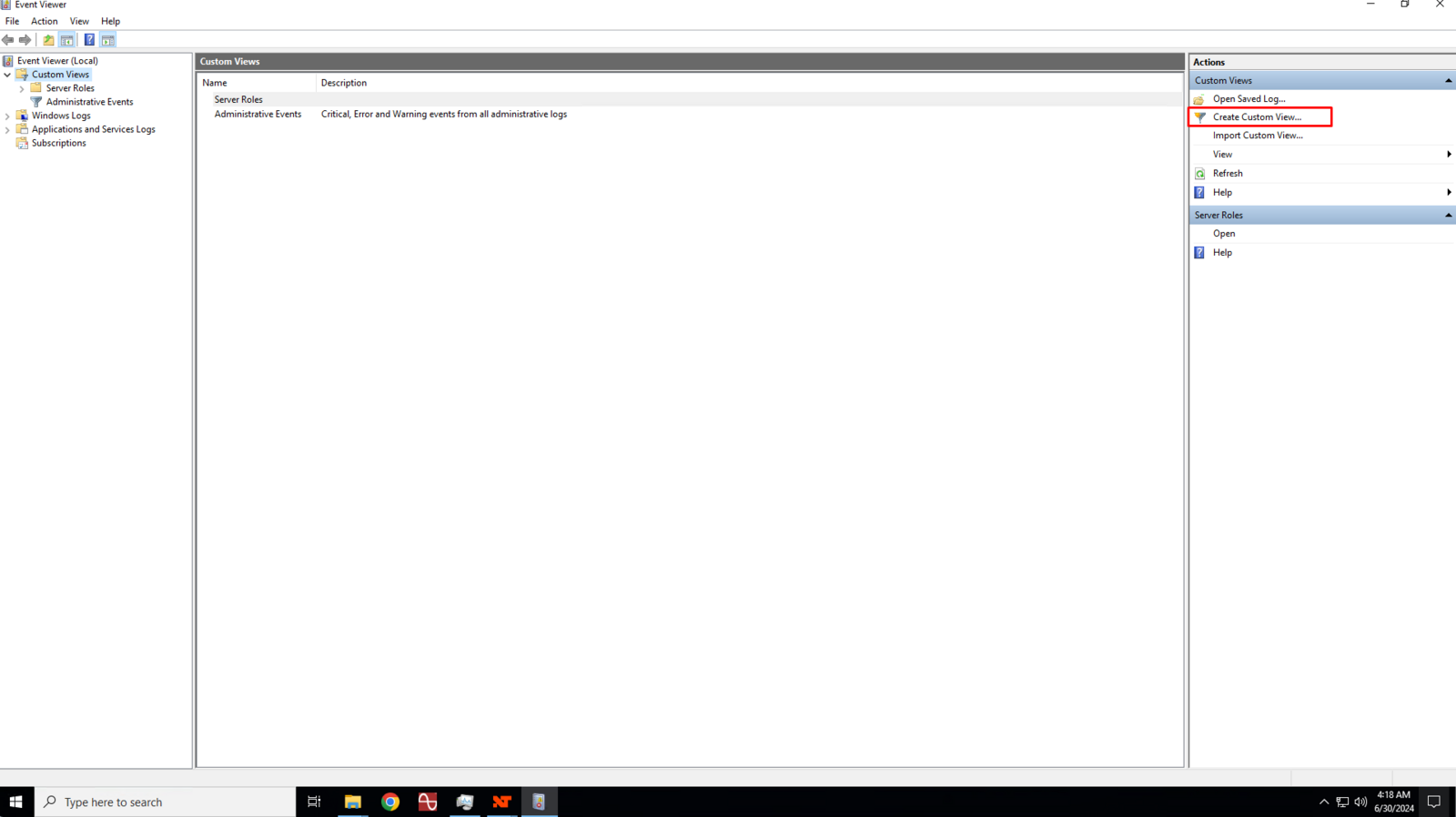
Are you struggling to understand what’s happening on your network? Knowing how to check network logs can be a game-changer for keeping your system secure and running smoothly.
These logs hold the key to spotting problems early, tracking down errors, and even stopping cyber threats before they cause damage. You’ll learn simple, clear steps to access and read your network logs—no tech jargon, just practical advice you can use right away.
Keep reading, and take control of your network like a pro.
Importance Of Network Logs
Network logs record details about data moving through a network. They help track activities and events on devices.
These logs are important for keeping networks secure and running smoothly. They show what is happening in real time.
Role In Troubleshooting
Network logs help find and fix problems quickly. They show errors and warnings that explain issues.
Technicians use logs to see when and where a problem started. This helps avoid downtime and loss of data.
- Identify failed connections
- Detect unusual traffic
- Trace source of errors
- Monitor device performance
Types Of Network Logs
There are different types of network logs. Each type records specific information about network activity.
Knowing these types helps you understand what to look for when checking logs.
- Firewall Logs:Show blocked or allowed network traffic.
- Router Logs:Record data about routing and device status.
- Switch Logs:Track network switch activity and errors.
- Server Logs:Log server access and system events.
- Intrusion Detection Logs:Detect possible security threats.
Preparing To Check Logs
Checking network logs helps find problems and improve security. Before you start, you need to get ready.
Proper preparation saves time and makes the process easier. This section covers what tools you need and how to access devices.
Gathering Necessary Tools
You need the right tools to check network logs correctly. These tools help you view and analyze the data.
Common tools include software and hardware that connect to the network and collect logs.
- Computer with network access
- Log viewer software like Wireshark or Syslog Viewer
- Credentials to access network devices
- Network cables or wireless adapters
- Text editor for reading log files
Accessing Network Devices
You must connect to your network devices to check their logs. Devices include routers, switches, and firewalls.
Access may be through a web interface, SSH, or a console cable. Make sure you have permission and correct login details.
- Use a web browser to open the device’s IP address
- Use SSH client like PuTTY for command line access
- Connect physical console cables if remote access is disabled
- Confirm you have admin or user rights to view logs
Common Log Sources
Network logs help track activity and find problems. They come from different devices in a network.
Knowing where logs come from helps you check them faster. Common sources include routers, firewalls, and servers.
Router And Switch Logs
Routers and switches control data flow in a network. They create logs about traffic and errors.
These logs show connection attempts, dropped packets, and configuration changes.
- Traffic volume and direction
- Interface status changes
- Security alerts
- Hardware errors
Firewall Logs
Firewalls monitor and control network access. Their logs record allowed and blocked traffic.
They help identify threats and unauthorized access attempts to your network.
- Blocked connection attempts
- Allowed traffic details
- Rule changes
- Intrusion alerts
Server Logs
Servers run applications and store data. Their logs track system events and user activity.
These logs help find errors and monitor performance of software and hardware.
- Login and logout events
- Application errors
- Resource usage
- System warnings and crashes

Credit: alparslanakyildiz.medium.com
Reading Log Entries
Network logs show details about data moving through a system. Reading these logs helps find problems or check activity.
Logs contain many entries. Each entry tells a part of the story about what happened on the network.
Understanding Log Formats
Logs use different formats depending on the system. Knowing the format helps you read entries correctly.
Common log formats include text lines with fields separated by spaces or commas. Each field shows specific data.
- Timestamp: When the event happened
- Source IP: The sender’s address
- Destination IP: The receiver’s address
- Protocol: Type of network protocol used
- Status Code: Success or error details
Identifying Key Information
Focus on important parts in each log entry. This helps you understand the network activity clearly.
Look for source, destination, time, and status. These details show who did what and if it worked well.
- Check timestamps to track event order
- Note IP addresses to find communication points
- Watch protocol types to know the traffic kind
- Look for error codes to spot problems
Using Log Analysis Tools
Network logs store important data about all network activities. They help find problems and improve security.
Log analysis tools make it easier to read and understand these logs. They organize data and show useful insights.
Popular Software Options
Many software tools help analyze network logs. Each has features to fit different needs and skill levels.
- Splunk: Collects and searches large log files quickly.
- Wireshark: Captures and inspects network packets in detail.
- Graylog: Offers easy log management and alert features.
- Loggly: Cloud-based tool for real-time log monitoring.
- ELK Stack: Combines Elasticsearch, Logstash, and Kibana for powerful log analysis.
Automating Log Review
Automating log review saves time and finds issues faster. Tools can check logs without human help.
Automation uses alerts and reports to notify about unusual events. This helps fix problems early.
- Set rules to detect errors or attacks automatically.
- Use scheduled scans to review logs regularly.
- Get email or message alerts for critical issues.
- Combine with machine learning for smarter analysis.
Troubleshooting Techniques
Network logs record all activities in a network. Checking these logs helps find problems fast.
We use logs to see errors and unusual actions. This helps fix network issues effectively.
Isolating Network Issues
Look at network logs to find where the problem starts. Check for error messages or failed connections.
Focus on the time and device causing the issue. This helps narrow down the exact cause quickly.
- Check logs for error codes or warnings
- Note the time stamps of issues
- Identify devices involved in errors
- Look for patterns in repeated failures
Tracking Unauthorized Access
Network logs show who accessed the system and when. Watch for unknown users or strange times.
Look for repeated login failures or access from unusual locations. These signs may mean a security risk.
- Check for unknown IP addresses
- Monitor failed login attempts
- Watch access outside normal hours
- Look for changes in user permissions
Best Practices For Log Management
Network logs help track activities and find problems. Managing logs well keeps your network safe.
Good log management means checking logs often and storing them securely. This helps find issues fast.
Regular Log Review
Look at your network logs every day or week. This helps find unusual actions early. Set a schedule to review logs.
Use automated tools to scan logs for errors or warnings. This saves time and catches issues you might miss.
- Check logs for strange login attempts
- Look for repeated error messages
- Watch for unusual data transfers
- Keep records of your reviews
Secure Log Storage
Store logs in a safe place to stop unauthorized access. Use encryption to protect log files.
Keep backup copies of logs in different locations. This prevents data loss if one storage fails.
- Use strong passwords for log access
- Limit who can view or change logs
- Encrypt logs during storage and transfer
- Keep backups in secure, separate places
Credit: learn.microsoft.com
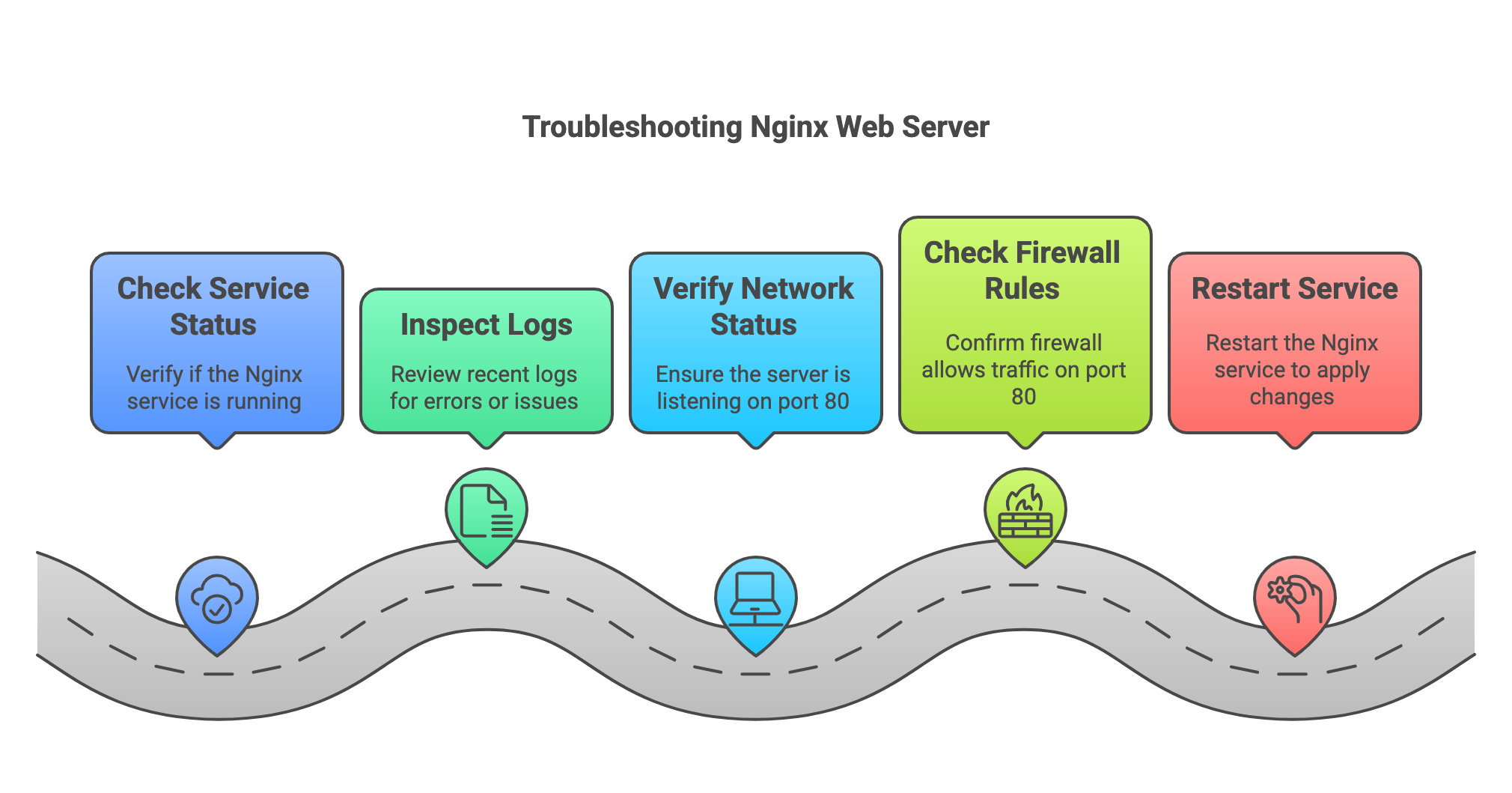
Credit: levelup.gitconnected.com
Frequently Asked Questions
What Are Network Logs And Why Check Them?
Network logs are records of network activity and events. Checking them helps identify issues, track access, and improve security by monitoring traffic patterns and detecting anomalies.
How Do I Access Network Logs On My Device?
Access network logs via your device’s settings or network management tools. Common methods include using command-line utilities or logging features in routers and firewalls.
Which Tools Are Best For Checking Network Logs?
Popular tools include Wireshark, SolarWinds, and Splunk. These provide detailed insights, real-time monitoring, and easy log analysis for troubleshooting and security purposes.
How Often Should Network Logs Be Reviewed?
Review logs regularly, ideally daily or weekly. Frequent checks help quickly spot problems, unauthorized access, and maintain optimal network performance and security.
Conclusion
Checking network logs is crucial for maintaining system health. It helps identify issues early and ensures smooth operations. Regular monitoring can prevent potential problems. Use the right tools to simplify the process. Keep logs organized for easy access and analysis.
Always update your skills and knowledge. This ensures you handle any network situation efficiently. Practice makes the process easier over time. Stay consistent with your efforts. Your network’s performance depends on it. Remember, a well-maintained network enhances productivity. Keep learning and adapting to new methods.
Your dedication will pay off in the long run.
14 min read