Setting up your network the right way can save you from countless headaches down the road. Whether you’re managing a small office or a growing business, missing just one crucial step in your network configuration can lead to slow connections, security risks, or even downtime.
This Network Configuration Checklist is designed to guide you through every essential task, so you don’t overlook what matters most. Keep reading, and you’ll gain the confidence to build a network that’s fast, secure, and reliable—protecting your work and giving you peace of mind.
Assess Network Requirements
Before setting up a network, you must know what it needs. Assessing requirements helps build a strong network.
This step saves time and money by planning for the right tools and setup.
Identify Devices And Users
List all devices that will connect to the network. Include computers, printers, phones, and other gadgets.
Also, count the number of users who will access the network at the same time.
- Desktop and laptop computers
- Smartphones and tablets
- Printers and scanners
- Smart home devices
- Guest users and employees
Determine Bandwidth Needs
Bandwidth is the data the network sends and receives. Know how much bandwidth your users need.
Consider activities like video calls, file downloads, and web browsing that use more data.
- Video streaming requires high bandwidth
- Simple browsing needs less bandwidth
- File sharing uses moderate bandwidth
- Online gaming needs low latency and stable bandwidth
Plan Network Layout
Design the physical and logical setup of your network. Decide where devices and cables will go.
Good layout reduces problems and makes the network faster and easier to manage.
- Place routers and switches centrally
- Use wired connections for stationary devices
- Plan Wi-Fi zones for good coverage
- Label cables and ports clearly

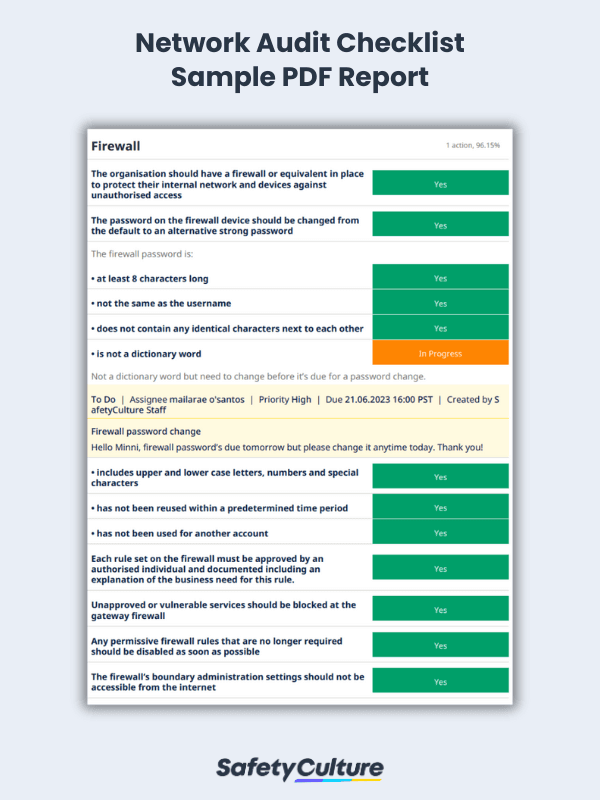
Credit: safetyculture.com
Choose Secure Hardware
Choosing secure hardware is key to protecting your network. Good hardware helps stop attacks and keeps data safe.
Invest in devices that offer strong security features. This lowers risks and improves network performance.
Select Reliable Routers And Switches
Pick routers and switches from trusted brands. They should support the latest security protocols.
Look for hardware with built-in encryption and regular software updates. This helps block unauthorized access.
- Supports WPA3 or higher encryption
- Offers automatic firmware updates
- Has strong password and login controls
- Includes intrusion detection features
Implement Firewalls
Firewalls protect your network by filtering incoming and outgoing traffic. They stop harmful data from entering.
Use hardware firewalls that fit your network size. They add a strong layer of defense against cyber threats.
- Block unauthorized access
- Monitor network traffic
- Allow safe data through
- Provide alerts on suspicious activity
Use Network Access Control Devices
Network Access Control (NAC) devices verify who can connect to your network. They enforce security rules for devices.
NAC devices help stop infected or unknown devices from joining. They keep your network clean and safe.
- Authenticate users and devices
- Check device security status
- Limit access based on policies
- Isolate risky devices automatically
Set Up Ip Addressing
Setting up IP addressing is key for network communication. Every device needs a unique IP address.
This setup helps devices find each other and share data smoothly. Proper addressing avoids conflicts.
Assign Static And Dynamic Ips
Static IPs do not change and stay assigned to a device. They are useful for servers and printers.
Dynamic IPs change over time and are given by a DHCP server. They work well for most user devices.
- Use static IPs for important devices that need a fixed address
- Use dynamic IPs for everyday devices like laptops and phones
- Keep a list of static IP addresses to avoid conflicts
Configure Subnets
Subnets divide a large network into smaller parts. This helps organize and manage traffic better.
Each subnet has its own range of IP addresses. Devices in the same subnet communicate faster.
- Choose subnet masks based on the number of devices
- Use smaller subnets to improve security and reduce traffic
- Plan subnets to match departments or locations
Implement Dhcp Settings
DHCP automatically assigns IP addresses to devices on a network. It saves time and reduces errors.
Set DHCP scopes to control which IPs can be assigned. You can also set lease times for addresses.
- Define IP address ranges for DHCP to use
- Set lease duration based on how long devices stay connected
- Reserve IP addresses for devices needing static assignment
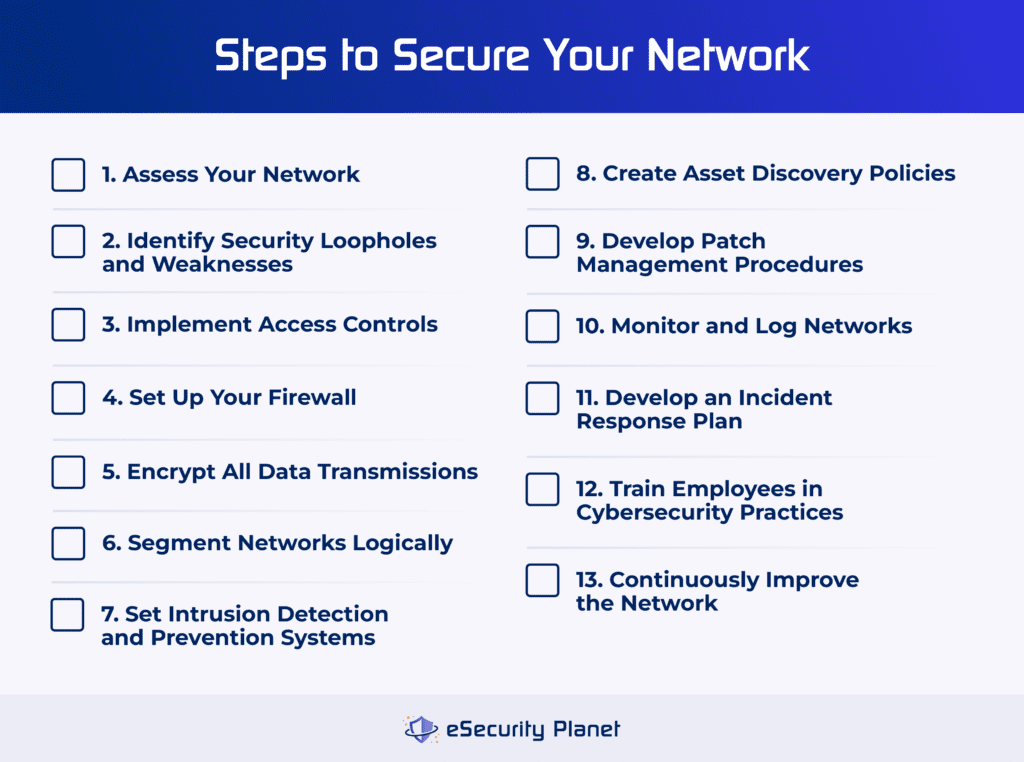
Credit: www.esecurityplanet.com
Configure Network Protocols
Network protocols control how devices communicate. Setting them right keeps your network safe and fast.
Good protocol configuration stops attacks and improves data flow. Follow this checklist to secure your network.
Enable Secure Communication Protocols
Use secure protocols to protect data during transfer. They prevent eavesdropping and data theft.
Protocols like HTTPS, SSH, and TLS encrypt information. This keeps your network communications private and safe.
- Activate HTTPS for web traffic
- Use SSH for secure remote access
- Enable TLS for email and messaging
- Disable older, insecure protocols like Telnet
Disable Unused Services
Turning off unused services reduces security risks. Each active service can be a target for hackers.
Check all running services and stop those not needed. This lowers the chance of network breaches.
- List all active network services
- Identify services not in use
- Disable or uninstall those services
- Regularly review running services
Update Firmware And Software
Keep firmware and software up to date. Updates fix security holes and improve performance.
Check for updates from device makers often. Apply them quickly to protect your network.
- Schedule regular update checks
- Install firmware patches promptly
- Update network software frequently
- Test updates before full deployment
Implement Access Controls
Access controls protect your network from unwanted users. They help keep data safe and secure.
Strong access controls limit who can see or change important information. This lowers the risk of attacks.
Set Strong Passwords And Credentials
Use passwords that are hard to guess. Mix letters, numbers, and symbols for better security.
Change default passwords right away. Avoid using the same password for many accounts.
- Use at least 12 characters
- Include uppercase and lowercase letters
- Add numbers and special characters
- Change passwords every 3 to 6 months
Use Multi-factor Authentication
Multi-factor authentication adds a second step to login. This step can be a code or a fingerprint.
This extra step makes it harder for hackers to access accounts. Even if they have the password, they need more.
- Use SMS or email codes
- Use authentication apps like Google Authenticator
- Enable biometric checks if available
Define User Roles And Permissions
Assign roles to users based on their job tasks. This limits what each user can do.
Only give access needed to perform work. Avoid giving full control to everyone.
- Admin: Full access to all settings
- Editor: Can change content but not settings
- Viewer: Can see data but not edit

Credit: softwareg.com.au
Establish Firewall Rules
Setting up firewall rules is key to protecting your network. Firewalls control which traffic can enter or leave.
Good firewall rules stop unwanted access and keep trusted data flowing smoothly.
Block Unnecessary Ports
Close ports that your network does not use. Open ports can let in harmful traffic.
Only open ports for services you need. This lowers the risk of attacks.
- Scan your network to find open ports
- Identify which ports are needed for your apps
- Close all other ports on your firewall
Allow Trusted Traffic Only
Permit connections from known and safe sources only. This reduces chances of intrusions.
Use rules to whitelist IP addresses or ranges that are trusted. Block all others by default.
- List trusted IP addresses
- Create firewall rules to allow these IPs
- Set default rule to block unknown traffic
Monitor Firewall Logs
Check firewall logs regularly to see blocked and allowed traffic. Logs help find problems.
Look for unusual activity, such as many blocked attempts from one source. This may signal attacks.
- Review logs daily or weekly
- Identify repeated blocked IPs
- Update rules based on log findings
Enable Network Encryption
Network encryption helps keep your data safe from hackers. It turns your information into a secret code.
Using encryption protects your network and privacy. It is an important step in network security.
Use Vpns For Remote Access
VPNs create a secure connection for remote users. They encrypt data sent over the internet.
VPNs hide your IP address and location. This makes it harder for attackers to spy on your connection.
- Use strong VPN protocols like OpenVPN or WireGuard
- Require VPN use for all remote workers
- Update VPN software regularly
Encrypt Wireless Networks
Wireless networks are easy targets for hackers. Encrypting Wi-Fi stops others from reading your data.
Use strong Wi-Fi encryption standards. WPA3 is the best option for most networks today.
- Set a strong Wi-Fi password
- Disable WPS to improve security
- Change default router settings
Apply Tls/ssl For Data Transmission
TLS and SSL protect data sent between computers. They encrypt web traffic like emails and websites.
Use TLS/SSL to secure online forms, logins, and payments. This keeps data private and safe.
- Install SSL certificates on web servers
- Force HTTPS connections for all users
- Renew certificates before they expire
Monitor And Maintain Network
Keeping your network healthy is very important. You need to watch it closely and fix problems fast.
Regular checks help stop issues before they get big. Good tools and plans make this easier.
Set Up Network Monitoring Tools
Network monitoring tools watch your system all the time. They send alerts if they find problems.
These tools track traffic, device status, and possible attacks. They help you fix issues quickly.
- Check network speed and uptime
- Watch for unusual activity or errors
- Get alerts for failures or slowdowns
Schedule Regular Audits
Audits are planned checks of your network setup. They find weak spots and outdated parts.
Set dates to review security, devices, and traffic. Fix problems before they cause trouble.
- Check firewall and security settings
- Review device and software updates
- Test network performance and backups
Plan For Backup And Recovery
Backups save your important data in safe places. Recovery plans help restore data fast after a failure.
Create backup schedules and test recovery steps. This keeps your network running without long stops.
- Back up data daily or weekly
- Store backups offsite or in the cloud
- Practice recovery to check your plan
Frequently Asked Questions
What Is Network Configuration?
Network configuration involves setting up a network’s controls, flow, and operation. It includes tasks like assigning IP addresses, setting up routers and switches, and enabling network security protocols. Proper configuration ensures efficient, secure, and reliable network operations.
Why Is Network Configuration Important?
Network configuration is crucial for maintaining security, performance, and reliability. It ensures that devices communicate efficiently and securely. Proper configuration minimizes downtime and enhances data protection. It also aids in troubleshooting and optimizing network performance.
How To Create A Network Configuration Checklist?
Start by identifying network requirements and devices. Include steps for IP address assignment, security settings, and equipment setup. Regularly update the checklist to accommodate new technology and security protocols. A comprehensive checklist helps streamline network setup and maintenance.
What Are Common Network Configuration Errors?
Common errors include incorrect IP address assignments, misconfigured routers, and weak security settings. These can lead to connectivity issues and security vulnerabilities. Regular audits and updates help prevent these mistakes, ensuring a stable and secure network.
Conclusion
A solid network setup keeps your system safe and fast. Follow each step on the checklist carefully. Check your settings often to avoid problems. Keep passwords strong and update software regularly. Clear, simple actions protect your data and devices. Use this guide as a regular reminder.
A well-configured network helps you work without interruptions. Stay alert and maintain your network for best results.
19 min read