Are you worried about keeping your network safe from hackers and unwanted traffic? Setting up firewall rules is one of the best ways to protect your devices and data.
But if you’re new to this, the process might seem confusing or overwhelming. Don’t worry—this guide will walk you through each step clearly and simply. By the end, you’ll have the confidence to create strong firewall rules that keep your digital world secure.
Ready to take control of your network’s safety? Let’s dive in.

Credit: bryanrenzy.medium.com
Firewall Basics
A firewall is a security tool that controls network traffic. It helps protect computers from unauthorized access.
Setting up firewall rules helps keep your data safe by allowing or blocking certain connections.
What Is A Firewall
A firewall is a system that monitors incoming and outgoing network traffic. It decides whether to allow or block data packets.
Firewalls create a barrier between a trusted network and an untrusted network like the internet.
Types Of Firewalls
There are different types of firewalls used for security. Each type works in a unique way.
- Packet Filtering Firewall: Checks data packets one by one.
- Stateful Inspection Firewall: Tracks active connections for better control.
- Proxy Firewall: Acts as a gateway between users and the internet.
- Next-Generation Firewall: Combines traditional functions with extra security features.
Firewall Roles In Security
Firewalls help protect networks by blocking harmful traffic. They also allow safe data to pass through.
Firewalls stop hackers, viruses, and unwanted access to your network.
- Control access to networks and devices.
- Monitor data for suspicious activity.
- Prevent unauthorized users from entering.
- Help enforce security policies in organizations.
Preparing For Firewall Setup
Setting up firewall rules is important to protect your network. It blocks unwanted traffic and keeps your data safe.
Before creating rules, you must prepare well. This helps your firewall work efficiently and avoid mistakes.
Assessing Network Needs
Know your network layout and devices. Understand what needs protection and what traffic is normal.
Check how users connect and what services run on the network. This helps to set accurate rules.
- List all devices and servers
- Identify allowed applications and services
- Note trusted IP addresses and networks
- Understand normal traffic patterns
Identifying Potential Threats
Think about what risks your network faces. This includes hackers, malware, and unauthorized access.
Look at past security problems and common attacks in your industry. This helps in making strong rules.
- Recognize common attack types
- Note weak spots in your network
- Watch for unusual traffic or access
- Plan to block harmful sources
Choosing The Right Firewall
Select a firewall that fits your network size and needs. It should support the features you require.
Consider ease of use, update options, and support. These factors help keep your firewall effective.
- Check compatibility with your hardware
- Look for good logging and alert tools
- Choose firewalls with regular updates
- Consider budget and scalability
Creating Effective Rules
Firewall rules control network traffic to keep systems safe. Good rules stop bad traffic and allow good traffic.
Creating clear and simple rules makes your firewall work well. This guide explains how to set up strong rules.
Allow Vs Deny Rules
Allow rules let traffic pass through the firewall. Deny rules block traffic from entering or leaving.
Use allow rules for trusted services and deny rules for unknown or risky traffic. Be careful with allow rules.
- Allow rules open ports or IPs you trust
- Deny rules stop unwanted connections
- Start with deny all, then allow what you need
Setting Up Inbound Rules
Inbound rules control traffic coming into your network. Only allow traffic that you expect or need.
Check which services need inbound access. Block all other ports and IP addresses by default.
- Allow inbound traffic for web servers or email
- Deny unused ports to reduce risk
- Use IP filters to limit access
Configuring Outbound Rules
Outbound rules manage traffic leaving your network. Control what users or apps can connect to outside networks.
Allow only necessary outbound connections. Block suspicious or unnecessary traffic to protect your data.
- Allow outbound traffic for software updates
- Deny unknown or risky external addresses
- Limit outbound traffic by application or protocol
Prioritizing Rules
Firewall rules are checked in order. The first matching rule applies to the traffic.
Put specific rules before general ones. This ensures important rules work correctly.
- Place deny rules before allow rules for security
- Order rules from most to least specific
- Review rule order often to avoid mistakes
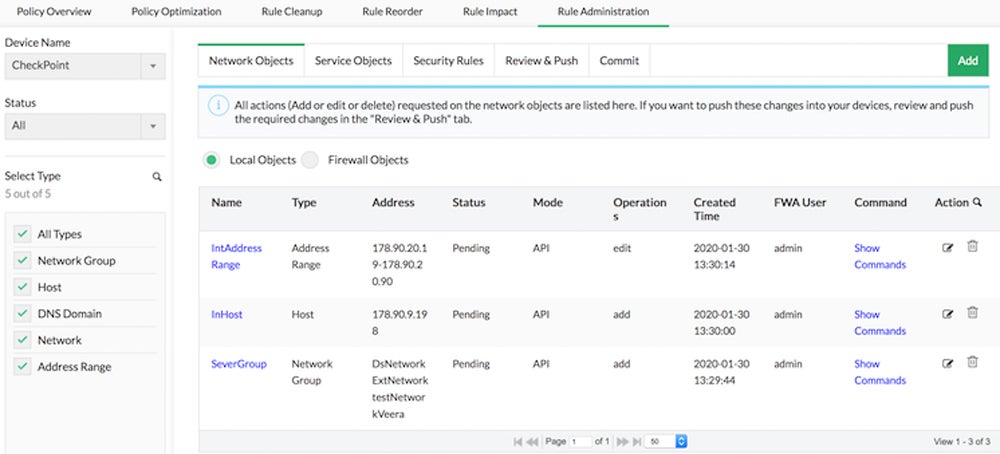
Credit: www.esecurityplanet.com
Common Rule Configurations
Firewall rules control the flow of data in and out of your network. Setting them right keeps your system safe and running smoothly.
Understanding common firewall rules helps you protect against threats and allow needed traffic.
Blocking Malicious Traffic
Firewalls stop harmful data from entering your network. You can block traffic from bad IP addresses or known attack sources.
Use blacklist rules to deny access to suspicious locations or patterns.
- Block IP addresses linked to attacks
- Stop traffic from suspicious countries
- Prevent access to dangerous websites
- Filter out unusual data packets
Allowing Trusted Services
Some services need access to your network. Firewalls must allow trusted services to work without interruption.
Create rules that let specific applications or IP addresses pass safely.
- Allow traffic from known software updates
- Permit connections from company servers
- Enable access for payment systems
- Whitelist IPs of cloud services
Managing Port Access
Ports let data flow to specific services on your network. Open only ports needed for your work.
Close unused ports to reduce risks from hackers.
| Port Number | Service | Rule Action |
|---|---|---|
| 80 | HTTP Web Traffic | Allow |
| 443 | HTTPS Secure Web | Allow |
| 23 | Telnet (Unsecure) | Block |
| 21 | FTP | Allow (If needed) |
Handling Vpn And Remote Access
VPNs let remote users access your network safely. Firewalls must allow VPN traffic but keep it secure.
Set rules to control who can connect and what they can access.
- Allow VPN protocols like IPsec and OpenVPN
- Restrict remote access to certain IPs
- Use strong authentication for VPN users
- Monitor VPN connections for unusual activity
Testing And Monitoring
Setting up firewall rules is only the first step. Testing and monitoring keep your network safe. They help find weak spots and improve security.
Regular checks ensure your firewall works well. You can fix problems before they cause damage.
Validating Rule Effectiveness
Test your firewall rules by simulating attacks or using security tools. This shows if rules block unwanted traffic.
Check if allowed traffic passes through without issues. Confirm rules do not stop important connections.
- Run penetration tests on the network
- Use automated tools to scan firewall
- Test both inbound and outbound traffic
- Verify allowed services work correctly
Using Logs For Insights
Firewall logs record all blocked and allowed connections. Review them often to spot unusual activity.
Look for repeated block attempts or strange IP addresses. Logs show if rules protect well or miss threats.
- Check logs daily or weekly
- Focus on denied traffic entries
- Identify patterns of attacks or errors
- Use log analysis tools for easier review
Adjusting Rules Based On Feedback
Use test results and logs to improve firewall rules. Remove rules that block safe traffic.
Add rules to block new threats or tighten weak spots. Keep firewall rules updated for best security.
- Fix false positives that block good traffic
- Add rules for new attack patterns
- Remove outdated or unused rules
- Repeat testing after changes
Advanced Firewall Features
Firewalls protect networks by controlling incoming and outgoing traffic. Advanced features make firewalls smarter and more secure.
These features help detect threats, filter applications, and manage users effectively. Understanding them improves your network safety.
Intrusion Prevention Systems
An Intrusion Prevention System (IPS) scans network traffic for harmful activity. It blocks threats before they enter your system.
IPS uses known attack patterns to find and stop attacks in real time. It keeps your network safe from hackers and malware.
- Monitors all network traffic continuously
- Detects suspicious activities and attacks
- Blocks threats automatically without delay
- Updates attack signatures regularly
Application Layer Filtering
Application Layer Filtering checks traffic based on the application data. It controls what apps can send or receive data.
This filtering stops unsafe apps and blocks bad content like viruses or harmful scripts. It protects users from web threats.
- Inspects data inside web pages and emails
- Blocks unauthorized or risky applications
- Allows only safe content to pass
- Improves control over network use
User And Group Policies
User and Group Policies let you set firewall rules for specific people or groups. This controls who can access what on the network.
Policies help limit access based on roles. They make sure users only see data and apps they need for work.
- Create rules for individual users or groups
- Restrict access to websites and services
- Apply different policies for departments
- Track user activity for security audits
Best Practices For Maintenance
Setting up firewall rules is important to protect your network. Keeping these rules updated keeps your system safe.
Regular checks help catch problems early. Follow these best practices to maintain your firewall well.
Regular Updates
Update your firewall software often to fix bugs and add new features. This keeps attackers from using old weaknesses.
Also, review your firewall rules regularly. Remove rules that are no longer needed to reduce risk.
- Install software updates quickly
- Check for outdated or unused rules
- Test changes before applying to live systems
Backup And Recovery
Always back up your firewall settings. This helps restore your system fast if something goes wrong.
Keep backups in a safe place. Test recovery procedures so you know they work well.
- Create backups after every major change
- Store backups separately from the firewall device
- Practice restoring backups regularly
Continuous Security Audits
Check your firewall rules often to find weak spots. Use security tools to scan for risks.
Review logs to see unusual activity. Adjust rules based on findings to improve protection.
- Schedule regular audits of firewall rules
- Analyze logs for suspicious traffic
- Update rules to block new threats

Credit: www.esecurityplanet.com
Frequently Asked Questions
What Are Firewall Rules?
Firewall rules are security measures that control incoming and outgoing network traffic. They determine which data packets are allowed or blocked, protecting your network from unauthorized access. Properly configured rules enhance security by allowing only legitimate traffic while preventing malicious activities.
How Do You Configure Firewall Rules?
To configure firewall rules, access your firewall settings through its interface. Define rules based on your security requirements. Specify the source, destination, and type of traffic. Save your settings and monitor the traffic to ensure your rules are effective.
Why Are Firewall Rules Important?
Firewall rules are crucial for network security. They help prevent unauthorized access and protect sensitive data. By controlling traffic, they minimize risks from cyber threats. Properly configured rules ensure only trusted data enters or leaves your network, maintaining system integrity.
What Is The Difference Between Inbound And Outbound Rules?
Inbound rules control traffic entering your network, while outbound rules manage traffic leaving it. Inbound rules protect against unauthorized access by allowing only trusted traffic. Outbound rules ensure sensitive data doesn’t leave your network without authorization, preventing data breaches.
Conclusion
Setting up firewall rules protects your network from threats. Start with clear rules based on your needs. Test each rule to ensure it works correctly. Keep rules simple and avoid too many exceptions. Review and update rules regularly to stay secure.
Good firewall rules help keep your data safe. Stay alert and adjust rules as your network grows. A strong firewall is key to online safety.
19 min read