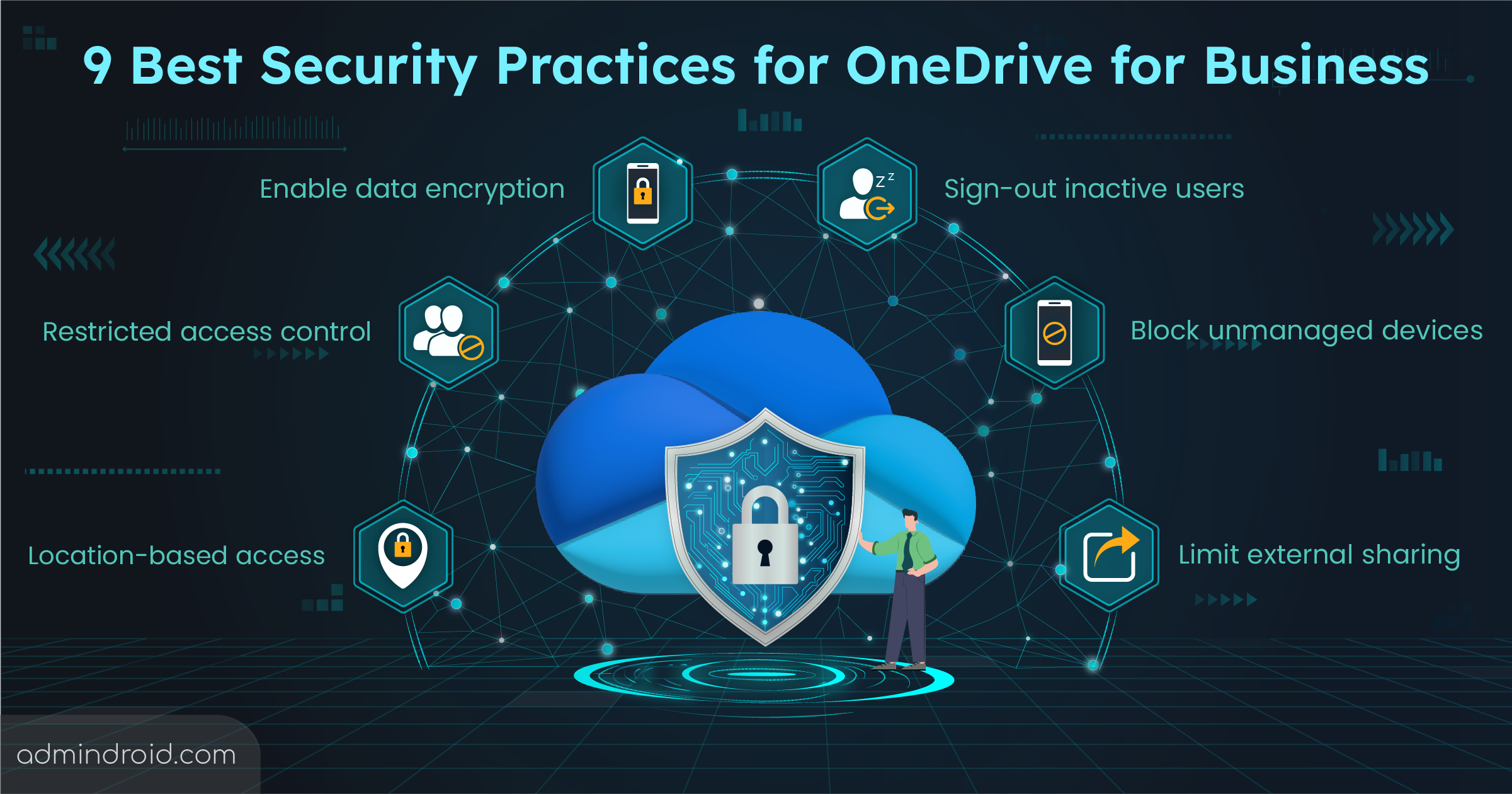
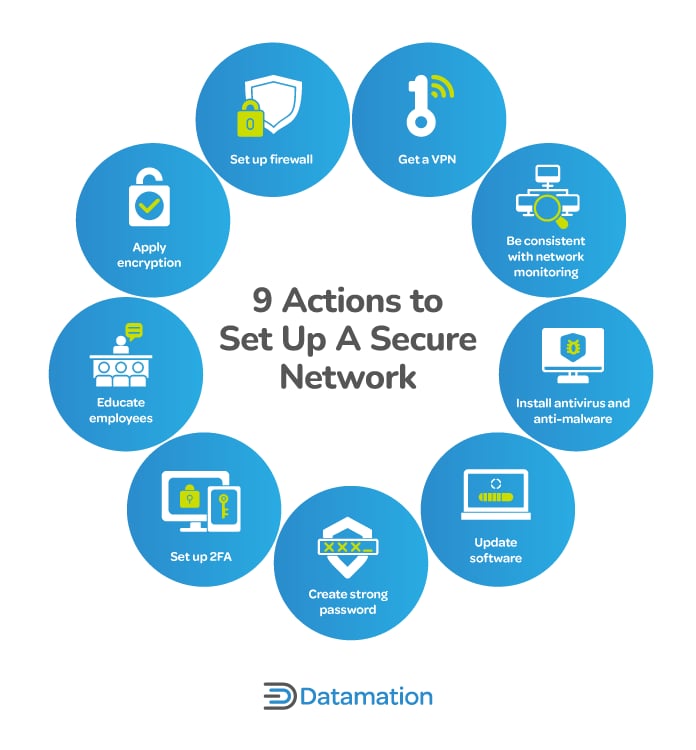
Are you confident that your security measures are truly protecting what matters most? Whether it’s your personal data, your business, or your devices, following the best practices in security can make all the difference between safety and vulnerability.
You’ll discover simple yet powerful steps you can take right now to strengthen your defenses. Keep reading to learn how to stay one step ahead of threats and protect your world with ease.
Strong Password Strategies
Strong passwords protect your accounts from hackers. Using good password habits keeps your information safe.
Learn how to create strong passwords, use tools to manage them, and update passwords regularly.
Creating Complex Passwords
Complex passwords are harder to guess or crack. Use a mix of letters, numbers, and symbols.
Avoid simple words or common phrases. Make your password long and unique for each account.
- Use uppercase and lowercase letters
- Add numbers and special characters
- Make passwords at least 12 characters long
- Don’t use personal information
Using Password Managers
Password managers store your passwords safely. They create and remember strong passwords for you.
This tool helps avoid reusing passwords and keeps your accounts more secure without extra effort.
- Choose a trusted password manager
- Use it to generate complex passwords
- Save all your passwords in one place
- Protect the manager with a strong master password
Regular Password Updates
Change passwords often to reduce risk. Regular updates stop hackers from using old passwords.
Set reminders to update passwords every few months. Update passwords after any security breach.
- Change passwords every 3 to 6 months
- Update passwords if you suspect hacking
- Use new, unique passwords each time
- Avoid minor changes like adding a number
Multi-factor Authentication
Multi-Factor Authentication (MFA) adds extra steps to log in. It helps protect your accounts from hackers.
MFA uses more than one way to verify your identity. This makes your accounts safer than using only a password.
Benefits Of Mfa
MFA stops most attacks that use stolen passwords. It makes it harder for others to access your data.
It also helps protect your personal and work accounts. Using MFA lowers the chance of identity theft.
- Stronger account security
- Less risk of data theft
- Protection even if password leaks
- Peace of mind for users
Types Of Mfa Methods
MFA can use different ways to prove who you are. Some methods are easy to use, others are very secure.
Here are common MFA methods you can try to secure your accounts.
- SMS Codes:Receive a code via text message.
- Authenticator Apps:Use apps like Google Authenticator for time-based codes.
- Biometrics:Use fingerprints or face scans.
- Hardware Tokens:Physical devices that generate login codes.
Implementing Mfa Across Accounts
Turn on MFA for all important accounts. Start with email, banking, and social media.
Check each service’s security settings. Follow their steps to set up MFA quickly and safely.
- Use authenticator apps for better security
- Keep backup codes in a safe place
- Enable MFA on work and personal accounts
- Update your MFA settings if you change devices
Secure Network Practices
Keeping your network safe is important to protect your data. Secure network practices help stop hackers.
Using simple steps can make your internet connection much safer. Let’s look at some key practices.
Using Vpns
A VPN hides your internet activity from others. It creates a secure tunnel for your data.
VPNs keep your information private, especially on public or shared networks.
- Choose a trusted VPN provider
- Turn on VPN before browsing
- Use VPN on all devices
Securing Wi-fi Connections
Secure your Wi-Fi to stop strangers from accessing your network. Use strong passwords.
Keep your router’s firmware updated to fix security holes and improve protection.
- Set a complex Wi-Fi password
- Use WPA3 or WPA2 encryption
- Change default router settings
- Turn off WPS for extra safety
Avoiding Public Networks
Public Wi-Fi can be risky because others may spy on your data. Avoid using it for sensitive tasks.
If you must use public Wi-Fi, do not access important accounts or share personal info.
- Use mobile data for secure browsing
- Turn off sharing options on your device
- Enable firewall and antivirus software

Credit: www.sentinelone.com
Software And System Updates
Keeping your software and systems up to date is very important for security. Updates fix bugs and close security gaps.
Ignoring updates can leave your system open to attacks and data loss. Regular updates help protect your data.
Importance Of Regular Updates
Regular updates improve system stability and security. They fix known problems and prevent hackers from exploiting weaknesses.
Updating software keeps all features working properly and reduces downtime. It also helps meet compliance rules.
Automating Patches
Automating patch installation saves time and reduces human errors. It ensures updates are applied quickly and consistently.
Automatic updates help close security holes faster. They keep your system safer without needing manual checks every day.
- Set up automatic update schedules
- Test patches in a controlled environment
- Monitor update success and failures
Handling Legacy Systems
Legacy systems may not support new updates. They can create risks if left unpatched or unsupported.
Plan to upgrade or isolate legacy systems. Use extra security measures to protect these older systems.
- Identify all legacy systems in use
- Apply available security patches
- Limit network access to these systems
- Plan for system replacement or upgrade
Data Backup And Recovery
Data backup and recovery help protect your important files. They keep your information safe from loss or damage.
Regular backups and a clear recovery plan ensure you can restore data fast. This reduces downtime and stress.
Backup Methods
There are different ways to back up data. Choose a method that fits your needs and budget.
- Full backup: Copies all data every time
- Incremental backup: Backs up only new or changed files
- Differential backup: Saves changes since the last full backup
- Cloud backup: Stores data on internet servers
- Local backup: Uses external drives or local servers
Frequency Of Backups
How often you back up data depends on how often it changes. Frequent backups reduce data loss risk.
Daily backups are common for active businesses. Some need hourly backups for critical data.
- Daily backups for most users
- Hourly backups for important systems
- Weekly backups for less active data
- Monthly backups for archives
Testing Recovery Plans
Testing your recovery plan shows if your backups work well. It helps find problems before real disasters.
Run tests by restoring files from backup. Check if all data is complete and usable.
- Schedule regular recovery tests
- Document steps to restore data
- Train staff on recovery procedures
- Fix any issues found during tests
Recognizing Phishing Attacks
Phishing attacks try to trick you into giving personal data. These scams look real but are fake.
Learning to spot phishing helps keep your information safe. It is important to stay alert.
Common Phishing Techniques
Phishers use many tricks to fool people. They often pretend to be trusted sources.
- Fake emails that look like banks or companies
- Links that lead to dangerous websites
- Urgent messages asking for personal information
- Attachments with harmful software
- Phone calls pretending to be support staff
Spotting Suspicious Emails
Check the sender’s address carefully. It may look real but be slightly off.
Look for bad spelling and grammar. Legitimate companies usually write well.
- Unexpected emails asking for passwords or payment
- Links that do not match the supposed sender
- Emails that create a sense of urgency or fear
- Attachments you did not expect
- Requests to click links or download files
Responding To Phishing Attempts
Do not click on any links or download files from suspicious emails. Delete the email immediately.
Report the phishing attempt to your email provider or IT team. They can help protect others.
- Mark the email as spam or phishing
- Do not reply to the sender
- Use security software to scan your device
- Change passwords if you shared any details
- Stay informed about new phishing methods
Device Security Measures
Keeping your devices safe helps protect your personal data. Simple actions can stop many security risks.
Use strong security steps on all devices like phones, laptops, and tablets. This keeps your information private.
Encrypting Devices
Encryption changes your data into a code to block unauthorized access. It protects your files if a device is lost or stolen.
Most modern devices have built-in encryption features. Turn on full disk encryption to secure all stored data.
- Use device settings to enable encryption
- Choose strong passwords for encryption keys
- Keep backup copies of important encrypted data
Using Security Software
Security software helps protect your device from viruses and malware. It can also block unsafe websites and downloads.
Keep security software updated to defend against new threats. Use software from trusted sources only.
- Install antivirus and anti-malware programs
- Run regular scans to find and remove threats
- Enable firewalls for extra protection
Physical Security Tips
Protect your devices from physical theft or damage. Keep them in safe places and avoid leaving them unattended.
Use locks or security cables for laptops. Be mindful of your surroundings when using devices in public.
- Store devices in locked drawers or cabinets
- Use screen privacy filters in public spaces
- Never share your device password or PIN
- Report lost or stolen devices immediately

Credit: qualysec.com
Employee Security Awareness
Employee security awareness is key to protecting a company. Workers must understand security risks and how to avoid them.
Good security habits from employees reduce threats from phishing, malware, and data leaks.
Training Programs
Regular training helps employees learn about the latest security threats. It also teaches how to respond to incidents.
Training should be clear and easy to follow. It can include videos, quizzes, and real-life examples.
- Teach password safety and management
- Explain how to spot phishing emails
- Show proper data handling practices
- Practice safe internet use
Promoting Security Culture
A strong security culture makes everyone responsible for safety. Employees feel motivated to protect company data.
Encourage open talks about security and reward good behaviors. Leaders should set a good example.
- Share security tips regularly
- Recognize employees who follow rules
- Make security part of daily work
- Keep communication clear and simple
Regular Security Audits
Security audits check how well employees follow security rules. They find weak spots before attackers do.
Audits can include tests, surveys, and system checks. Feedback helps improve training and policies.
- Test employee response to phishing emails
- Review access controls and permissions
- Survey staff about security knowledge
- Update policies based on audit results
Access Control Management
Access control management helps protect your data and systems. It ensures only the right people can see or use important information.
Good access control lowers risks and keeps your systems safe from unauthorized users.
Role-based Access
Role-based access gives users permissions based on their job roles. This limits access to only what they need to do their work.
Assigning roles helps simplify management and reduces errors in giving access rights.
- Define clear roles for each user type
- Grant permissions that fit each role
- Review roles regularly to update access
Least Privilege Principle
The least privilege principle means giving users the smallest access needed to do their tasks. This lowers the chance of mistakes or misuse.
Users should not have extra rights that they do not need. This keeps your system safer.
- Limit access to essential functions only
- Remove permissions when no longer needed
- Use temporary access for special tasks
Monitoring Access Logs
Access logs show who accessed what and when. Monitoring these logs helps find unusual or unauthorized activity quickly.
Regular checks of access logs improve security and help fix problems fast.
- Record all access events with user details
- Review logs daily or weekly
- Set alerts for suspicious actions

Credit: www.tatvasoft.com
Frequently Asked Questions
What Are The Essential Best Practices For Security?
Essential best practices include strong passwords, regular updates, multi-factor authentication, and employee training. These measures reduce vulnerabilities and protect sensitive data effectively.
How Often Should Security Protocols Be Updated?
Security protocols should be reviewed and updated at least quarterly. Frequent updates address new threats and ensure systems stay protected against evolving cyber risks.
Why Is Employee Training Crucial For Security?
Employee training prevents human errors, which cause many breaches. Educated staff recognize phishing, handle data securely, and follow safety policies consistently.
What Role Does Multi-factor Authentication Play In Security?
Multi-factor authentication adds a second verification layer, enhancing account protection. It significantly reduces unauthorized access, even if passwords are compromised.
Conclusion
Adopting these security practices protects your data and privacy. Strong passwords are crucial. Change them regularly. Keep software updated. This prevents vulnerabilities. Use two-factor authentication. It adds an extra security layer. Be cautious with emails and links. Avoid suspicious ones.
Regularly back up your data. Store it securely. Educate yourself on new threats. Stay informed and prepared. These steps help shield your online presence. Security is an ongoing effort. Stay vigilant. Protect your digital life.
20 min read