Are you struggling to control who can access your network and what they can do once inside? Making network access profiles is the key to securing your digital space without complicating your workflow.
Imagine having clear rules that decide who gets in, what they see, and how they interact—all set up quickly and easily. You’ll discover simple steps to create effective network access profiles that protect your data and keep your systems running smoothly.
Ready to take control of your network like a pro? Let’s dive in.
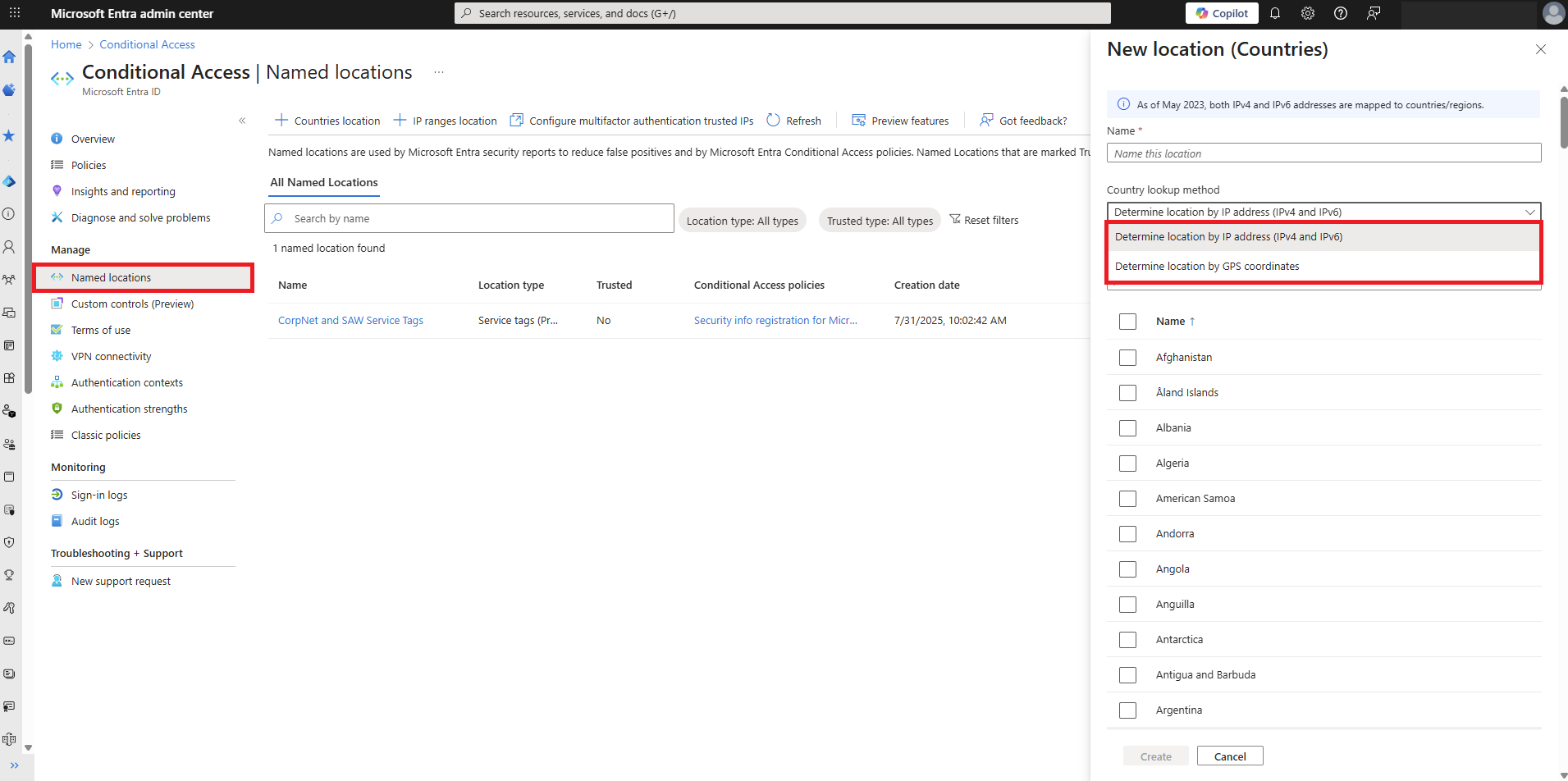
Credit: www.esecurityplanet.com
Network Access Profiles Basics
Network Access Profiles help control how devices connect to a network. They set rules for access and security.
These profiles make network management easier and protect sensitive data. They are important for all network users.
Purpose And Benefits
Network Access Profiles define who can use the network and how. They improve security by limiting access.
They also help manage network resources and reduce risks from unauthorized devices.
- Control device access to networks
- Protect sensitive information
- Improve network performance
- Reduce unauthorized access risks
Key Components
Profiles include settings like device type, user role, and connection method. These define access limits.
They also include security rules such as encryption and authentication requirements.
- Device identity and type
- User roles and permissions
- Connection types (wired or wireless)
- Security protocols and encryption
- Authentication methods
Common Types
There are several types of network access profiles. Each fits different network needs and users.
Examples include guest access, employee access, and admin access profiles.
- Guest Access:Limited network use for visitors
- Employee Access:Standard access for staff members
- Admin Access:Full control for network administrators
- Device-Based Access:Access based on device type
Credit: www.vonage.com
Designing Secure Profiles
Creating network access profiles helps protect your system. These profiles control who can use the network and what they can do.
Secure profiles reduce risks and keep data safe. Design profiles carefully for better network security.
Assessing Network Requirements
First, understand what the network needs. Look at the types of users and devices that will connect.
Check the data sensitivity and the kind of access users require. This helps set proper limits.
User And Device Segmentation
Divide users and devices into groups based on their roles and security levels. This keeps sensitive areas safe.
Separate devices like computers, phones, and printers. This stops threats from spreading across the network.
- Create groups for employees, guests, and contractors
- Segment devices by type and security needs
- Limit access between different groups
Role-based Access Control
Assign network permissions based on user roles. Only allow access to what users need for their jobs.
Use clear roles like admin, staff, or visitor. This keeps permissions simple and easy to manage.
- Define roles with specific access rights
- Grant minimum access needed for tasks
- Review and update roles regularly
Implementing Profiles
Network access profiles help control who can connect to your network. They define rules for devices and users.
Implementing these profiles means setting clear rules and managing access efficiently. It improves network security and performance.
Configuration Best Practices
Start with simple profiles and add details later. Test profiles in a small environment before full use.
Use clear names for profiles and document settings. Keep security settings updated to protect the network.
- Define clear access rules
- Test profiles before deployment
- Use descriptive profile names
- Regularly update security settings
- Document profile changes
Integration With Existing Systems
Network profiles should work well with your current systems. Check compatibility with your directory and authentication tools.
Connect profiles to user databases to assign access automatically. Use standard protocols for better integration.
- Verify system compatibility
- Link profiles to user directories
- Use standard protocols like LDAP or RADIUS
- Ensure smooth data exchange
- Maintain consistent user access
Automation Tools
Automation tools help create and update profiles faster. They reduce manual work and errors.
Use scripts or software that sync profiles with user changes. Set rules to adjust access automatically.
- Use scripts for profile creation
- Automate profile updates with user changes
- Set rules for automatic access adjustments
- Monitor automation for errors
- Save time and improve accuracy
Monitoring And Maintenance
Network access profiles control who can connect to your system. Monitoring and maintenance keep these profiles safe and up to date.
Regular checks help prevent unauthorized access and fix issues quickly. This keeps your network strong and secure.
Continuous Access Auditing
Continuous auditing tracks who accesses the network and when. This helps spot unusual activity fast.
Audit logs show if someone tries to use the wrong profile or access restricted areas.
- Record all login attempts
- Check access times and locations
- Review logs regularly for signs of trouble
Updating Profiles For Threats
New threats appear every day. Updating profiles helps block these dangers before they harm your network.
Change access rules to close security gaps. Remove or limit profiles that no longer need access.
- Add multi-factor authentication if needed
- Remove inactive users
- Adjust permissions based on job roles
Handling Exceptions And Incidents
Sometimes users need special access or make mistakes. Handling these exceptions carefully keeps the network safe.
Respond quickly to incidents to stop threats. Fix problems and update profiles to prevent repeats.
- Verify and approve special access requests
- Investigate unusual login attempts
- Update profiles after security incidents
Troubleshooting Access Issues
Network access profiles control who can connect to your network. Problems with these profiles can block access.
Fixing access issues requires checking settings and using tools to find the root cause.
Common Problems
Users often face problems like denied access or slow connection. Profiles may have wrong permissions or rules.
Other issues include expired credentials, network policy conflicts, or device misconfigurations.
- Access denied due to incorrect permissions
- Expired or invalid user credentials
- Conflicting network policies
- Device not matching profile requirements
- Authentication server failures
Diagnostic Techniques
Start by checking user permissions and profile settings. Confirm credentials are valid and current.
Use logs and network tools to track where access fails. Test connectivity and authentication steps.
- Review access logs for error messages
- Ping the network to check connectivity
- Use authentication tools to verify credentials
- Check device compliance with profile rules
- Test with different user accounts
Resolution Strategies
Fix permission errors by updating profile rules. Renew or reset user credentials if expired.
Adjust network policies to remove conflicts. Ensure devices meet profile requirements before granting access.
- Correct profile permissions and roles
- Reset passwords or authentication tokens
- Update network policies to avoid conflicts
- Configure devices to meet access criteria
- Restart authentication services if needed
Future Trends In Network Access
Network access is changing fast. New ways help keep data safe and users connected. These changes focus on better control and smarter technology.
Understanding future trends helps businesses prepare for safer and easier access. This guide covers key ideas shaping network access profiles.
Zero Trust Models
Zero Trust means no one is trusted by default. Every user and device must prove they are allowed to access the network.
This model reduces risks by checking identity and device health every time. It stops attackers from moving inside the network.
- Verify users before access
- Check device security status
- Limit access to needed resources only
- Monitor all activity closely
Ai-driven Access Controls
Artificial Intelligence helps manage network access by learning normal user behavior. It can spot unusual actions fast.
AI adjusts access rules automatically. It improves security without slowing down users or admins.
- Detects threats in real-time
- Adapts access based on risk levels
- Reduces manual work for admins
- Supports faster response to attacks
Cloud-based Profiles
Cloud-based profiles store access settings online. Users can access networks securely from anywhere.
This approach supports remote work and multiple devices. It also simplifies updates and policy management.
- Centralizes profile management
- Supports flexible user access
- Improves scalability and speed
- Integrates with cloud apps easily
Credit: www.juniper.net
Frequently Asked Questions
What Are Network Access Profiles?
Network Access Profiles are configurations that manage how users and devices connect to networks. They define access permissions, security protocols, and authentication methods. By using these profiles, organizations can ensure secure and efficient network access, aligning with specific policies and compliance requirements.
They play a crucial role in maintaining network security and performance.
How To Create Network Access Profiles?
To create Network Access Profiles, identify user needs and network requirements. Use network management software to define access rules, security settings, and permissions. Ensure compliance with organizational policies. Test the profiles to confirm functionality and security. Regularly update profiles to address new security threats and changes in network usage.
Why Are Network Access Profiles Important?
Network Access Profiles enhance network security and efficiency. They ensure users and devices have appropriate access levels, reducing unauthorized entry risks. These profiles help organizations comply with security standards and regulations. By managing access centrally, they simplify network administration and improve overall performance, making them essential for modern IT infrastructure.
Can Network Access Profiles Improve Security?
Yes, Network Access Profiles significantly enhance network security. They enforce strict access controls and authentication methods, reducing unauthorized access risks. By defining user permissions and security protocols, they prevent potential breaches. Regular updates and monitoring ensure profiles adapt to emerging threats, maintaining robust security for the organization’s network.
Conclusion
Creating network access profiles helps keep your data safe. It lets you control who can connect and what they can do. Profiles make managing networks easier and more organized. You can set different rules for different users or devices. This way, you reduce risks and improve security.
Start with clear settings, test them, and update as needed. A good profile keeps your network running smoothly and securely. Simple steps lead to strong protection and better control.
16 min read