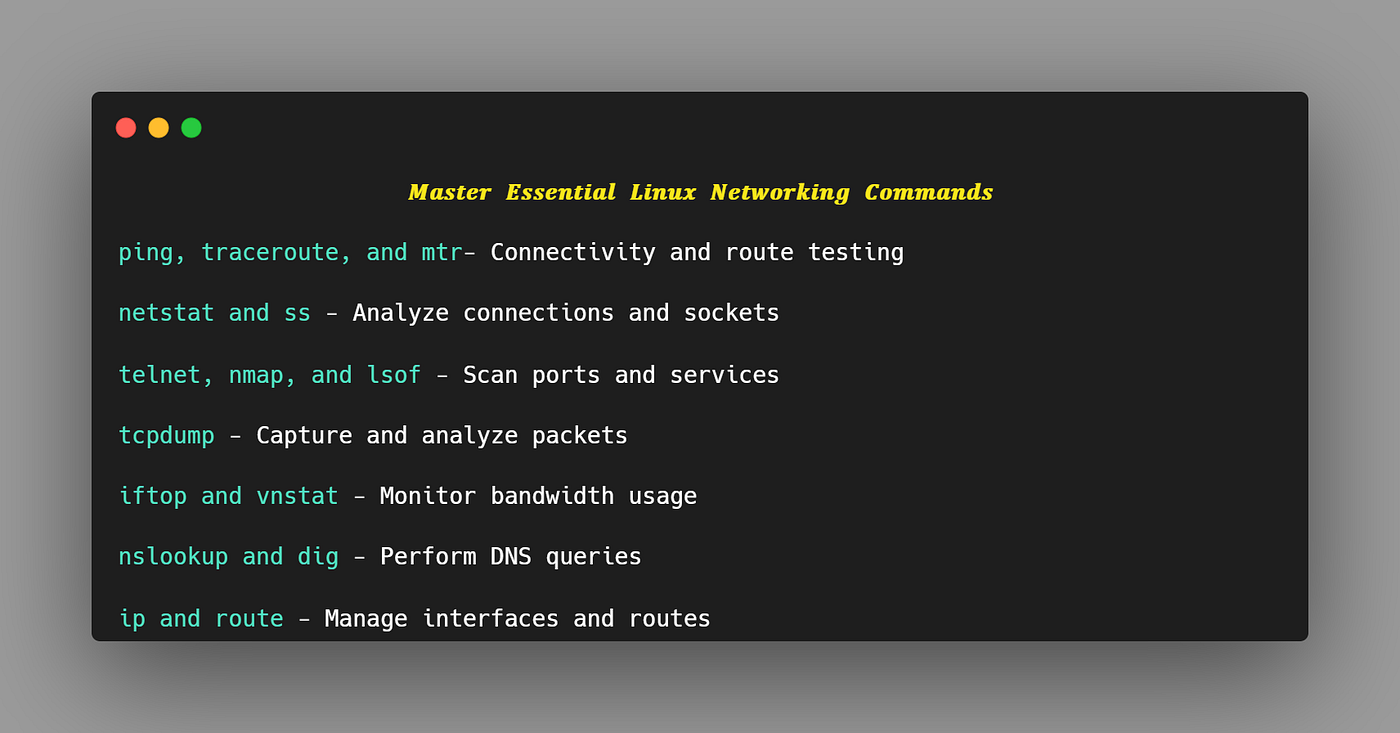
If you want to keep your network secure and running smoothly, understanding network logging is a must. Imagine having a clear, detailed record of everything happening in your network—every access attempt, every error, every unusual activity.
That’s what network logging does for you. It gives you the power to spot problems early, protect your data, and improve your system’s performance. You’ll discover the essential tools and techniques that make network logging work for you, even if you’re new to the topic.
Ready to take control of your network like a pro? Let’s dive in.

Credit: www.esecurityplanet.com
Basics Of Network Logging
Network logging records events and activities in a computer network. It helps track traffic, errors, and security issues.
Logs provide detailed information that network admins use to monitor and improve network performance.
What Network Logs Capture
Network logs capture data about devices and connections on the network. They show what happens over time.
Logs include information like IP addresses, timestamps, and the type of network activity.
- Source and destination IP addresses
- Time and date of events
- Type of network protocol used
- Errors and warnings
- Connection status and duration
Common Logging Protocols
Logging protocols set rules for how network data is recorded and sent. They help keep logs organized and readable.
Many devices use standard protocols to send logs to a central server for easier management.
- Syslog:A popular protocol for sending log messages.
- SNMP:Used for monitoring network devices and collecting data.
- NetFlow:Records IP traffic information for analysis.
- IPFIX:An extension of NetFlow with more details.
Types Of Network Logs
Different logs focus on various parts of the network. Each type helps track specific activities.
Admins use these logs to find problems or check for unusual behavior.
- Traffic Logs:Record data about network traffic and connections.
- Error Logs:Show network failures and device errors.
- Security Logs:Track access attempts and potential threats.
- System Logs:Contain information about network device operations.
Setting Up Effective Logging
Network logging helps track activity and find problems fast. Setting it up right keeps your network safe and running well.
Good logging needs clear steps and the right tools. This guide covers the basics to start logging effectively.
Choosing The Right Tools
Select tools that fit your network size and needs. Look for ease of use and strong security features.
Popular tools include open-source and commercial options. Choose ones that support your systems well.
- Check compatibility with your devices
- Ensure real-time logging capability
- Look for easy log searching and filtering
- Consider tools with alert features
Configuring Log Sources
Identify which devices and applications should send logs. Configure each to capture important events.
Set log levels to avoid too much or too little data. Focus on errors, warnings, and critical actions.
- Enable logging on firewalls and routers
- Include servers and key applications
- Use standard formats like syslog
- Test log collection to confirm setup
Establishing Log Retention Policies
Decide how long to keep logs based on rules and storage limits. Keep data long enough to investigate issues.
Set automatic deletion or archiving to manage space. Protect logs from unauthorized access.
- Follow legal and company rules for retention
- Keep logs for at least 30 days
- Archive older logs securely
- Review policies regularly
Analyzing Network Logs
Network logs record events happening in a network. Analyzing these logs helps find problems and security issues.
By studying network logs, you can understand how data moves and spot unusual activities early.
Detecting Anomalies
Anomalies are unusual patterns in network logs. They may show attacks or errors in the system.
Look for spikes in traffic, unknown IP addresses, or repeated failed logins. These signs can warn about threats.
- Sudden increase in data flow
- Access from strange locations
- Multiple login failures
- Unexpected changes in network behavior
Correlating Events
Correlating events means linking related log entries. This helps see the full story behind network actions.
By matching times and sources, you can find cause and effect or chains of suspicious activities.
- Match timestamps to track event sequences
- Group logs by IP address or user
- Identify related alerts from different devices
Using Automated Analysis
Automated tools scan logs quickly to find issues. They use rules and patterns to spot problems fast.
Automation reduces errors and saves time in monitoring large networks.
- Use software to detect known threats
- Set alerts for unusual activities
- Generate reports for easy review
Credit: www.geeksforgeeks.org
Enhancing Security With Logs
Network logging is a key part of keeping computer systems safe. Logs record events happening in the network.
These records help find problems and stop attacks before they cause damage.
Identifying Intrusions
Logs show unusual actions that may be signs of a break-in. They capture data like login attempts and data transfers.
By checking logs often, teams can spot strange patterns early. This helps stop intruders fast.
- Failed login attempts
- Unusual IP addresses
- Access at odd hours
- Large data downloads
Tracking Unauthorized Access
Logs help track who accessed the network without permission. They record user names and times of access.
This information shows what areas were reached and if data was changed or stolen.
- User ID and login time
- Files or systems accessed
- Duration of access
- Changes made to data
Supporting Incident Response
Logs give clear evidence during security incidents. They help teams understand what happened and how.
Good logs speed up fixing problems and stop attacks from spreading.
- Timeline of events
- Source of the attack
- Systems affected
- Actions taken
Optimizing Log Management
Network logging helps track activities and problems on a network. Good log management keeps data organized and easy to use.
Optimizing log management means saving space, keeping logs safe, and making logs easy to find.
Centralized Logging Solutions
Centralized logging collects all logs in one place. This makes it easier to search and analyze data.
It reduces the time spent checking many devices and improves problem-solving speed.
- Collect logs from all network devices
- Use a central server or cloud service
- Enable real-time monitoring
Handling Log Volume And Storage
Network logs can grow very fast and take much space. Managing this helps avoid storage problems.
Use methods like compression and log rotation to save storage and keep logs manageable.
- Compress old log files to save space
- Rotate logs to keep only recent data
- Archive important logs safely
Ensuring Log Integrity
Log integrity means keeping logs accurate and unchanged. This is key for trust and security.
Use checksums and access controls to protect logs from tampering or loss.
- Apply digital signatures or hashes
- Limit who can access or change logs
- Keep backup copies of logs
Future Trends In Network Logging
Network logging is essential for tracking system activities and security events. It helps organizations find issues and improve network performance.
New trends are shaping how network logging works. These trends bring better tools and faster responses to network problems.
Ai And Machine Learning Integration
Artificial intelligence (AI) and machine learning (ML) help analyze large sets of log data. They find patterns and detect unusual activities quickly.
These technologies reduce the time needed to spot threats or errors. They also help predict future network problems before they happen.
- Automated log analysis for faster issue detection
- Improved threat detection with pattern recognition
- Predictive alerts based on past network behavior
Cloud-based Logging Approaches
Cloud-based logging allows storing and managing logs online. This method offers flexibility and easy access from anywhere.
It helps teams collaborate and scale their logging needs without heavy hardware costs. Cloud logging also supports better data backup and recovery.
- Remote log storage with high availability
- Scalable solutions for growing network sizes
- Easy integration with other cloud services
Real-time Monitoring Advancements
Real-time monitoring shows network events as they happen. This helps teams react quickly to attacks or failures.
Advances in technology allow faster data processing and alerting. This keeps networks safer and reduces downtime.
- Instant alerts on suspicious activities
- Live dashboards for quick status checks
- Integration with automated response tools
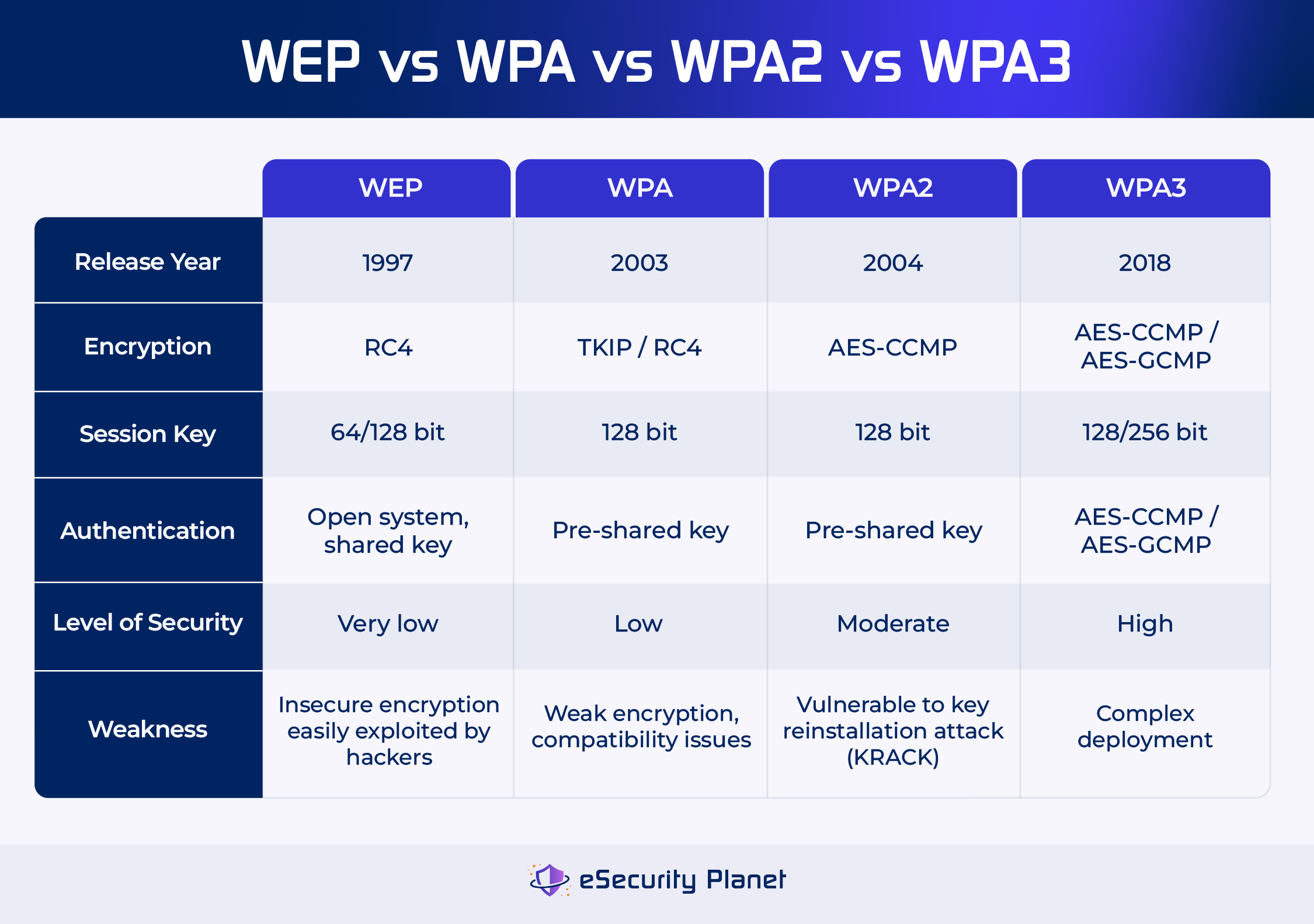
Credit: www.esecurityplanet.com
Frequently Asked Questions
What Is Network Logging And Why Is It Important?
Network logging records data about network activities and events. It helps in monitoring, troubleshooting, and securing networks efficiently.
How Does Network Logging Improve Cybersecurity?
Network logging tracks suspicious activities and unauthorized access. It provides valuable data for identifying and preventing cyber threats promptly.
What Are Common Tools Used For Network Logging?
Popular tools include Wireshark, Splunk, and SolarWinds. They help capture, analyze, and visualize network traffic and events.
How Often Should Network Logs Be Reviewed?
Network logs should be reviewed daily or weekly. Regular reviews help detect issues early and maintain network health.
Conclusion
Network logging plays a crucial role in maintaining network health. It helps you detect issues early. Logs offer insights into network performance. They provide valuable data for troubleshooting. Regular monitoring keeps your system secure. Understanding logs can prevent potential threats.
It’s essential for efficient network management. Embrace logging as a routine practice. By doing so, you enhance your network’s stability. This proactive approach ensures seamless operations. Stay informed and vigilant with network logging. Your network’s efficiency depends on it. Remember, a well-logged network is a well-protected one.
Keep logging, keep secure.
15 min read