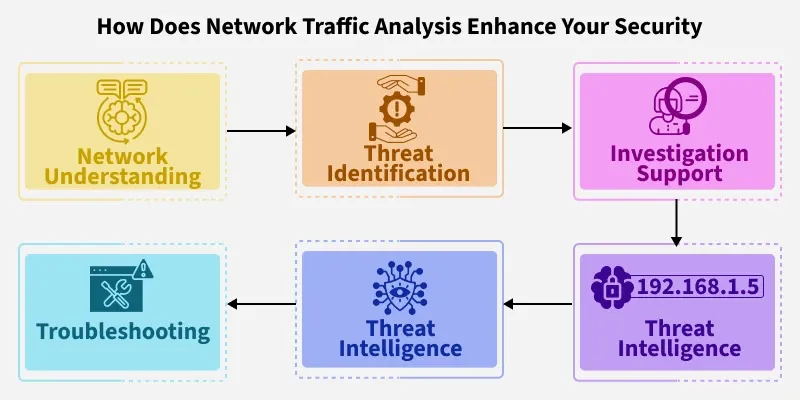
Are you confident that your network is running smoothly and securely? Understanding what flows through your network can be the key to preventing slowdowns, spotting threats, and making smarter decisions.
Network traffic analysis gives you a clear window into your data’s journey, helping you catch problems before they grow. You’ll discover how to unlock these insights easily and why mastering this skill can protect your business and boost your efficiency.
Ready to take control of your network like a pro? Keep reading.

Credit: medium.com
Basics Of Network Traffic
Network traffic is the flow of data across a computer network. It includes all the information sent and received between devices.
Understanding network traffic helps keep networks secure and running smoothly. It shows how data moves and what uses the network.
Types Of Network Traffic
Network traffic comes in different types based on its purpose. Each type serves a unique role in communication.
Some traffic carries emails or web pages. Other traffic helps devices connect or share files.
- Unicast: Data sent from one device to another device.
- Broadcast: Data sent to all devices in a network segment.
- Multicast: Data sent to a group of devices.
- Anycast: Data sent to the nearest device in a group.
Common Protocols And Their Roles
Protocols are rules that control how data moves in a network. They help devices talk to each other clearly.
Each protocol has a specific job, like sending emails or loading web pages.
- HTTP: Used to load web pages on your browser.
- FTP: Transfers files between computers.
- SMTP: Sends email messages.
- TCP/IP: Manages data delivery across networks.
- DNS: Translates website names into IP addresses.
Traffic Patterns And Behavior
Traffic patterns show how data moves over time. They help identify normal and unusual network use.
Some traffic flows steadily, while other traffic comes in bursts. Patterns vary by application and user activity.
- Periodic Traffic: Data sent at regular time intervals.
- Burst Traffic: Sudden spikes of data transmission.
- Interactive Traffic: Data exchanged during user actions.
- Background Traffic: Data sent without user interaction.

Credit: iritt.medium.com
Tools For Traffic Analysis
Network traffic analysis helps to understand data flow in a network. It shows how data moves and identifies problems.
Many tools exist to capture and study network traffic. They help keep networks safe and efficient.
Packet Sniffers And Analyzers
Packet sniffers capture data packets traveling across a network. They let you see the exact data sent and received.
Analyzers decode and display packet contents in a readable format. They help find errors and suspicious activity.
- Wireshark is a popular open-source packet analyzer.
- Tcpdump works in the command line to capture packets.
- Microsoft Network Monitor is used for Windows traffic analysis.
Flow Monitoring Tools
Flow monitoring tools track the flow of data between devices. They collect summaries instead of full packet details.
These tools help monitor traffic patterns and network usage over time. They are good for spotting trends and large data transfers.
- NetFlow by Cisco collects flow data from routers and switches.
- sFlow samples packets to provide traffic data across devices.
- IPFIX is a standard for exporting flow information.
Ai And Machine Learning Applications
AI tools analyze network traffic to find unusual patterns automatically. They improve threat detection and response time.
Machine learning models learn from past traffic data. They predict problems and alert administrators before issues grow.
- AI can detect malware by spotting strange traffic behaviors.
- Machine learning helps classify traffic by type and priority.
- These tools reduce manual analysis work for network teams.
Detecting Threats Through Traffic
Network traffic analysis helps find security problems by watching data flow. It checks how data moves to spot bad actions.
By looking at traffic, we can see when something is wrong or dangerous. This helps keep networks safe from attacks.
Identifying Anomalies
Anomalies are unusual changes in network data. They can show when something is not normal or suspicious.
Examples include sudden spikes in traffic or unknown devices connecting. These signs help find threats early.
- Unexpected data patterns
- Unusual connection times
- Traffic from unknown sources
- Changes in data size or type
Spotting Malicious Activities
Malicious activities include attacks like hacking or spreading viruses. Traffic analysis can detect these by watching bad behavior.
Signs include repeated failed logins, data leaks, or strange requests. Detecting these helps stop attacks fast.
- Multiple login failures
- Unusual data transfers
- Requests to suspicious sites
- High traffic from one source
Tracing Attack Origins
Tracing attack origins means finding where the bad traffic comes from. This helps understand and block threats.
Using IP addresses and traffic paths, you can follow the attack back to its source. This stops future attacks.
- Track IP addresses involved
- Analyze data routes
- Identify entry points
- Use logs to follow attacks
Optimizing Security With Traffic Insights
Network traffic analysis helps to find risks in real time. It gives details about data moving through the network.
Using traffic insights improves security by spotting unusual activity early. It helps teams act fast to protect data.
Real-time Monitoring Strategies
Real-time monitoring lets you see network traffic as it happens. This helps detect threats before they cause damage.
Tools can track traffic patterns, flagging anything that looks suspicious or out of place.
- Watch for sudden spikes in data flow
- Check for unknown devices on the network
- Alert on traffic to risky websites
Automated Response Systems
Automated response systems act fast when threats appear. They use rules to block or limit harmful traffic right away.
This reduces the time attackers have to do damage and keeps the network safer.
- Automatically block suspicious IP addresses
- Quarantine infected devices
- Send alerts to security teams
Policy Adjustments Based On Data
Traffic data helps update security rules and policies. This keeps defenses strong against new threats.
Teams use traffic insights to decide which actions improve network safety the most.
- Block risky protocols or ports
- Limit access for certain users or devices
- Improve firewall and VPN settings
Challenges In Network Traffic Analysis
Network traffic analysis helps monitor data moving through a network. It finds problems and protects against threats. But it faces many challenges. These challenges make analysis hard and slow.
Experts must find ways to handle big data, keep privacy, and reduce errors. Understanding these challenges helps improve network security and performance.
Handling Large Data Volumes
Networks produce huge amounts of data every second. Analyzing this data in real-time is difficult. Storage and processing need strong systems that work fast.
Too much data can slow down analysis tools. It is hard to find important information in large data streams.
- Requires high storage capacity
- Needs fast data processing
- Data filtering is essential
- Scalability is a must
Encryption And Privacy Issues
Many networks use encryption to keep data safe. Encryption hides the content of the traffic. This makes it harder to analyze what is inside the data.
Privacy rules limit what data can be checked. Analysts must respect laws and user privacy while monitoring network traffic.
- Encrypted data hides details
- Privacy laws restrict data access
- Balancing security and privacy is tough
- Need special tools for encrypted data
False Positives And Accuracy
Network tools sometimes flag normal traffic as a problem. These are false positives. They waste time and reduce trust in the system.
Improving accuracy is important. Accurate tools find real threats and avoid false alarms. This saves time and resources.
- False positives cause confusion
- Accuracy affects response speed
- Need better detection algorithms
- Regular updates improve results

Credit: medium.com
Future Trends In Traffic Analysis
Network traffic analysis studies data moving through computer networks. It helps detect threats and improve performance.
New technology changes how experts analyze network traffic. These trends will shape the future of network security.
Integration With Cloud Security
More businesses use cloud services for data and apps. Traffic analysis must work well with cloud security tools.
Combining traffic data from cloud and local networks helps find hidden threats. It gives a full view of network health.
- Monitors cloud traffic in real time
- Protects against cloud-based attacks
- Improves visibility across hybrid networks
Advances In Behavioral Analytics
Behavioral analytics studies user actions and patterns in network traffic. It helps spot unusual activity fast.
New tools use behavior data to detect insider threats and malware. These advances make traffic analysis smarter.
- Tracks normal user behavior over time
- Alerts on abnormal traffic patterns
- Helps prevent data breaches
Role Of Ai In Predictive Security
Artificial intelligence can predict security problems before they happen. AI analyzes traffic data to find weak points.
AI uses machine learning to improve detection and reduce false alarms. It helps teams respond faster to threats.
- Predicts potential attacks based on patterns
- Automates threat detection and response
- Supports continuous network monitoring
Frequently Asked Questions
What Is Network Traffic Analysis?
Network traffic analysis involves monitoring, capturing, and examining network data. It helps identify patterns, potential threats, and performance issues. By analyzing traffic, businesses can ensure network security and optimize performance. This process is crucial for maintaining a stable and secure network environment.
Why Is Network Traffic Analysis Important?
Network traffic analysis is vital for identifying security threats and optimizing performance. It helps detect unusual activities, ensuring the network remains secure. By understanding data flow, businesses can enhance efficiency and prevent downtime. This proactive approach safeguards valuable data and resources.
How Does Network Traffic Analysis Work?
Network traffic analysis works by capturing data packets traversing a network. Specialized tools monitor this data, identifying irregular patterns. These insights help in detecting potential threats or inefficiencies. Analyzing traffic ensures the network operates smoothly and securely, enhancing overall performance and reliability.
What Tools Are Used For Traffic Analysis?
Popular tools for network traffic analysis include Wireshark, SolarWinds, and PRTG Network Monitor. These tools capture and analyze network data, identifying issues and potential threats. They offer real-time monitoring, ensuring network security and optimal performance. Using the right tool can significantly enhance network management.
Conclusion
Network traffic analysis helps keep networks safe and fast. It shows where data flows and finds weak spots. This process stops threats before they cause harm. It also helps fix problems quickly. Using simple tools can make analysis easier for everyone.
Regular checks keep systems working well every day. Understanding traffic means better control and fewer surprises. Stay alert and use traffic data to protect your network. This keeps users happy and businesses running smoothly.
17 min read