Are you struggling to connect to your office network while working from home or on the go? Setting up remote network access might sound complicated, but it doesn’t have to be.
Imagine being able to access your files, applications, and resources securely from anywhere, as if you were right at your desk. You’ll discover simple steps to set up remote network access that keeps your data safe and boosts your productivity.
Keep reading, and you’ll soon have the confidence to manage your network connection effortlessly—no technical jargon or confusion required.
Benefits Of Remote Network Access
Remote network access lets users connect to their work network from anywhere. It helps businesses stay connected and flexible.
This setup supports many work styles and improves how teams work together. It also saves money and time.
Increased Flexibility
Remote access allows employees to work from different places. They can use any device with internet access.
This flexibility helps people balance work and life better. It also supports different time zones and schedules.
Enhanced Productivity
With remote network access, workers get quick access to files and apps. They can solve problems faster.
Teams can share information instantly. This reduces delays and keeps projects moving forward.
Cost Savings
Businesses save money on office space and equipment. Remote access lowers the need for physical resources.
It also cuts travel costs. Employees can join meetings online without spending on transport or hotels.

Credit: docs.ava.do
Types Of Remote Access
Remote network access lets users connect to a network from different locations. It helps employees work from home or while traveling.
There are several types of remote access. Each type offers different features and security levels.
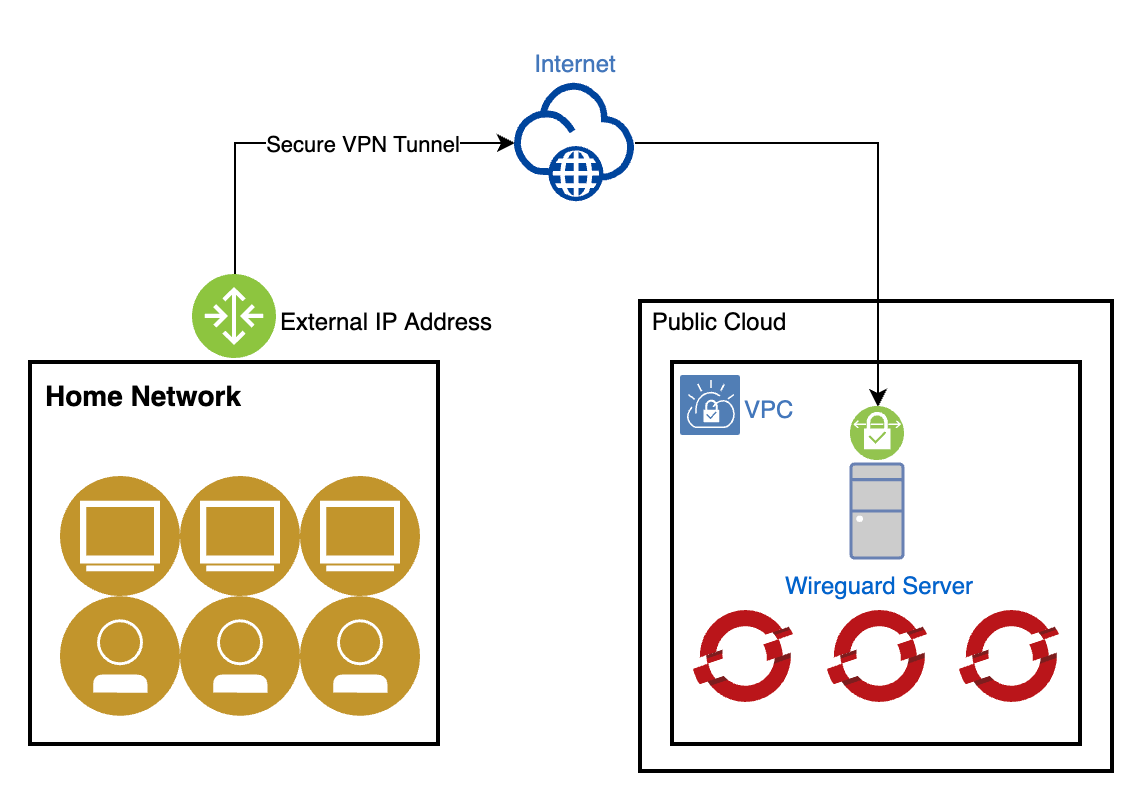
Virtual Private Network (vpn)
A VPN creates a secure connection between your device and the internet. It encrypts data to keep it safe from hackers.
VPNs let users access company resources as if they were in the office. This method is popular for its security and privacy.
- Encrypts internet traffic
- Hides your IP address
- Works on many devices
- Requires VPN client software
Remote Desktop Protocol (rdp)
RDP allows users to control a computer from another device. It shows the remote computer’s screen and lets you use its programs.
This type of access works well for IT support and remote work. Users need permission and proper security settings to use RDP.
- Access full desktop remotely
- Control apps and files
- Requires network permissions
- Best for Windows environments
Cloud-based Solutions
Cloud-based access uses the internet to connect to apps and data stored in the cloud. No special software is often needed.
These solutions offer easy access from any device. They are flexible and good for teams working in different places.
- Access apps via web browsers
- No need for VPN or RDP
- Works on phones, tablets, and PCs
- Cloud providers handle security
Essential Security Measures
Setting up remote network access needs strong security to protect data. Without it, hackers can steal information.
Use these key security steps to keep your network safe from attacks and unauthorized users.
Strong Authentication Methods
Strong authentication stops unauthorized users from entering your network. Use more than just a password.
Multi-factor authentication adds layers of security. It asks for something you know and something you have.
- Use passwords with letters, numbers, and symbols
- Enable multi-factor authentication (MFA)
- Use biometric options like fingerprint or face ID
Data Encryption
Data encryption changes your information into a secret code. This keeps it safe during transfer.
Encrypting data helps stop hackers from reading your files or messages if they get access.
- Use VPNs to encrypt remote access connections
- Encrypt sensitive files on devices
- Use HTTPS for web-based tools
Regular Software Updates
Keep your software updated to fix security bugs. Old software can let hackers enter your network.
Set devices to update automatically. Check for patches on security tools often.
- Update operating systems regularly
- Install patches for network devices
- Update antivirus and firewall software
Step-by-step Setup Process
Setting up remote network access lets users connect to your network from anywhere. This guide helps you create a safe and easy access system.
Follow these steps to plan, choose tools, and set permissions for remote access.
Assessing Network Requirements
First, find out what your network needs for remote access. Think about who will connect and what they need to do.
Check your network speed and security needs to avoid problems later.
- Identify users who need remote access
- List the resources users must reach
- Check your current network capacity
- Determine required security levels
Choosing The Right Tools
Select tools that fit your network size and user needs. The right tools make setup easier and keep data safe.
Look for tools that support your devices and offer good security features.
- Use VPNs for secure connections
- Consider remote desktop software
- Check compatibility with your devices
- Choose tools with encryption options
Configuring Access Permissions
Set clear access rules to protect your network. Only allow users to see what they need.
Use strong passwords and update permissions regularly to stay safe.
- Create user accounts for remote access
- Assign permissions based on user roles
- Enable multi-factor authentication
- Review access logs for unusual activity
Common Challenges And Solutions
Setting up remote network access can be tricky. Many face problems with connections and security.
This guide covers common challenges and simple ways to solve them for smooth remote access.
Handling Connectivity Issues
Remote users often struggle with slow or dropped connections. This can stop work and cause frustration.
Using reliable VPNs and checking internet quality helps keep connections stable and secure.
- Choose VPNs with strong servers
- Test internet speed before remote sessions
- Restart routers or devices if needed
- Use wired connections when possible
Preventing Unauthorized Access
Security is a top concern when allowing remote network access. Unauthorized users can cause damage.
Strong passwords, two-factor authentication, and firewalls help keep intruders out.
- Use unique, complex passwords
- Enable two-factor authentication
- Install and update firewall software
- Limit access by IP address or device
Managing User Access
Not all users need full network access. Managing permissions keeps data safe and limits risks.
Assign roles and review access regularly to ensure only the right people can enter.
- Create user groups with specific permissions
- Review access rights every few weeks
- Remove access for users who leave
- Use software to track login activity
Credit: medium.com
Best Practices For Maintenance
Setting up remote network access is important for work flexibility. Proper maintenance keeps the network safe and fast.
Regular checks and updates prevent problems. Follow these best practices to maintain a secure remote access system.
Monitoring Network Activity
Watch network activity to find unusual behavior early. This helps stop threats before they cause harm.
Use tools that track logins, data use, and connection times. Look for patterns that do not fit normal use.
- Check login attempts daily
- Review data transfer for spikes
- Alert on unknown device connections
Updating Security Protocols
Keep security settings current to protect your network. Updates fix weaknesses that hackers try to use.
Install patches and update software regularly. Use strong encryption and change passwords often.
- Apply software patches monthly
- Use VPNs with strong encryption
- Change passwords every 90 days
Training Users
Teach users how to use remote access safely. Good habits reduce the risk of security breaches.
Show users how to spot phishing emails and avoid unsafe Wi-Fi. Remind them to log out after sessions.
- Train on spotting phishing scams
- Encourage use of secure Wi-Fi only
- Remind to log out after use
Future Trends In Remote Access
Remote network access is changing fast. New ideas and tech will shape how people connect to networks. These changes aim to keep data safe and make access easier.
Understanding these trends helps companies prepare for the future. They can protect their information and support users better.
Zero Trust Networks
Zero Trust means never trusting any user or device by default. Every access request must be checked before allowing entry.
This model improves security by limiting who can see or use network resources. It stops attackers even if they get inside the network.
- Verifies every user and device
- Uses strict access controls
- Reduces risk of data breaches
Ai-driven Security
Artificial intelligence helps detect unusual network activity fast. It can spot threats before they cause harm.
AI tools learn normal user behavior. When something looks wrong, AI alerts security teams automatically.
- Monitors network traffic in real time
- Identifies suspicious access attempts
- Automates threat response
Improved User Experience
Remote access will become easier and faster for users. New tools reduce waiting time and simplify login steps.
Users will get smooth access across devices without losing security. This helps workers stay productive from anywhere.
- Single sign-on across apps
- Faster connection speeds
- Simple multi-factor authentication

Credit: hiruthicsha.medium.com
Frequently Asked Questions
How Do I Set Up Remote Network Access?
To set up remote network access, first configure your router’s settings. Ensure that port forwarding is enabled for the desired services. Use a VPN for secure connections. Install necessary software on remote devices. Test the connection to ensure everything is working correctly.
Always keep your network’s firmware updated for security.
What Equipment Is Needed For Remote Access?
For remote access, you’ll need a reliable router with VPN support. A computer or device with internet access is essential. VPN software or apps should be installed for secure connections. A stable internet connection is crucial. Finally, ensure your router’s firmware is up-to-date for optimal performance.
Is A Vpn Necessary For Remote Network Access?
Yes, a VPN is essential for secure remote network access. It encrypts your data, ensuring privacy and security. A VPN protects against cyber threats and unauthorized access. It also provides a stable and reliable connection. Always choose a reputable VPN service for the best security and performance.
How Can I Ensure Remote Access Security?
To ensure remote access security, use strong, unique passwords for network devices. Enable two-factor authentication if available. Regularly update your router’s firmware and software. Use a VPN for encrypted connections. Limit access to trusted devices only. Regularly monitor network activity for any suspicious behavior.
Conclusion
Setting up remote network access keeps your work flexible and secure. It helps you connect to your office from anywhere. Use strong passwords and encryption to protect your data. Regular updates keep your system safe from threats. Simple steps make remote access easier and safer.
Stay careful and enjoy the freedom to work remotely.
17 min read








