Are you worried about the security risks when guests connect to your Wi-Fi? You’re not alone.
When you share your network, you might be unknowingly opening doors to hackers or slowing down your internet. Using guest isolation networks can protect your personal data and keep your main network safe. Imagine giving your visitors internet access without giving them access to your private files or devices.
Curious how this works and why it matters? Keep reading to discover simple, effective steps you can take to secure your network right now.
Benefits Of Guest Isolation Networks
Guest isolation networks separate visitors from the main network. This helps keep your network safe and running well.
Many businesses use guest networks to give internet access to visitors. These networks stop guests from reaching private devices.
Enhancing Security
Guest isolation networks stop visitors from accessing secure parts of your network. This lowers the risk of attacks.
They block guests from seeing other devices. This keeps your computers and files safe from hackers.
- Limits access to sensitive devices
- Prevents spread of malware
- Reduces chance of data theft
Improving Network Performance
Guest networks keep visitor traffic separate from main users. This reduces network slowdowns.
With less traffic on the main network, critical tasks run faster and smoother.
- Reduces congestion on main network
- Improves speed for employees
- Helps maintain stable connections
Protecting Sensitive Data
Guest isolation networks keep personal and business data safe. Guests can only access the internet, not private files.
This separation stops accidental or intentional data leaks from visitors.
- Blocks access to confidential files
- Prevents data breaches
- Supports compliance with privacy rules

Credit: medium.com
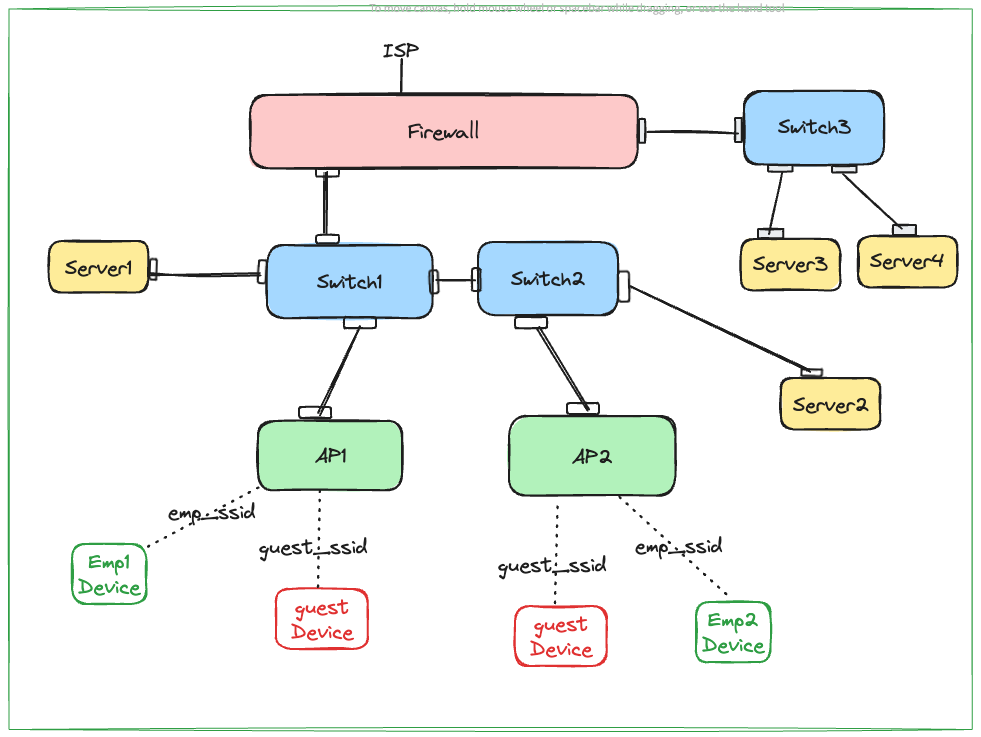
How Guest Isolation Works
Guest isolation networks keep visitors separate from main networks. This helps protect sensitive data and devices.
These networks limit what guests can see and access. They create a safer environment for both guests and hosts.
Network Segmentation Basics
Network segmentation divides a larger network into smaller parts. Each part works independently from the others.
This separation stops guests from reaching private systems. It also reduces the chance of spreading viruses or attacks.
- Separate guest and private networks physically or logically
- Use VLANs to create virtual network segments
- Assign different IP ranges to guest devices
Traffic Control Mechanisms
Traffic control manages data flow between networks. It decides which data can pass and which cannot.
Using firewalls and access points, the system blocks unwanted connections. It keeps guest traffic separate from private data.
- Firewalls filter guest network requests
- Access points isolate guest Wi-Fi traffic
- Bandwidth limits prevent network overload
Access Restrictions
Access restrictions limit what guests can use on the network. They stop guests from reaching sensitive files or devices.
Rules can block certain websites or services. They also prevent guests from connecting to private printers or servers.
- Block access to internal IP addresses
- Restrict file sharing and device discovery
- Set time limits for guest network use
Implementing Guest Isolation Networks
Guest isolation networks keep visitors’ devices separate from your main network. This protects your business data from unauthorized access.
Setting up guest isolation requires careful planning and proper configuration. It ensures safe and controlled internet access for guests.
Choosing The Right Hardware
Select hardware that supports multiple network segments or VLANs. This helps create separate guest networks easily.
Look for routers and access points with strong security features and guest network options.
- Routers with VLAN support
- Access points with guest network features
- Firewalls to control traffic between networks
- Devices that handle high traffic loads
Configuring Network Settings
Create a separate VLAN or subnet for guest devices. This keeps guest traffic isolated from your main network.
Set up DHCP to assign IP addresses only within the guest network range. Use firewall rules to limit access between networks.
- Enable VLAN tagging for guest traffic
- Configure separate DHCP server for guests
- Apply firewall rules to block internal network access
- Use bandwidth limits to control guest usage
Setting Up User Policies
Define clear rules for guest network use. Limit the time and data guests can access to protect resources.
Inform guests about acceptable use policies. Use login portals or passwords to control network access.
- Set session time limits
- Restrict access to sensitive sites
- Require user authentication if needed
- Monitor network activity for security
Credit: community.ruijie.com
Common Use Cases
Guest isolation networks help keep visitors’ devices separate from main networks. This improves security and privacy for everyone.
They are used in many places where people connect to shared Wi-Fi. Below are common examples of where guest isolation is helpful.
Corporate Environments
In offices, guest isolation networks protect company data. Visitors can use Wi-Fi without accessing sensitive systems.
It also stops guests from seeing or contacting employee devices on the network. This reduces risks of data leaks.
Public Wi-fi Spots
Places like cafes and airports offer guest Wi-Fi for customers. Isolation keeps each user’s device private and safe.
This setup prevents hackers from spying or attacking other users. It also helps control bandwidth and network traffic.
- Separates users from each other
- Blocks access to internal systems
- Limits risks of malware spreading
Educational Institutions
Schools use guest isolation to protect student and staff data. Visitors like parents or guests get internet access only.
This stops unauthorized access to school files and internal networks. It also helps manage network use during busy times.
Challenges And Solutions
Guest isolation networks help protect main networks from visitors. They create separate spaces for guests to use the internet safely.
These networks bring some challenges. Understanding these helps to find good solutions.
Managing Network Complexity
Guest isolation adds more parts to the network setup. This can make managing devices and connections harder.
Using clear network designs and simple rules can reduce confusion. Automating setup tasks also saves time.
- Use clear names for guest and main networks
- Set simple access rules for guests
- Automate IP address assignments
- Use tools to monitor network devices
Ensuring User Convenience
Guests expect easy and fast internet access. Complex logins or slow speeds can cause frustration.
Provide simple connection steps and good speed. Clear instructions help guests connect without problems.
- Offer a simple Wi-Fi name and password
- Use guest portals for easy login
- Limit bandwidth to keep speed fair
- Provide clear connection instructions
Monitoring And Maintenance
Networks need regular checks to stay secure and work well. Guest networks require special attention to avoid risks.
Track network use and fix issues fast. Update devices and security settings often to keep the network safe.
- Monitor guest traffic for unusual activity
- Check device connections regularly
- Update firmware and security patches
- Test network speed and access often

Credit: medium.com
Future Trends In Network Isolation
Network isolation helps protect devices and data from cyber threats. Guest isolation networks keep visitors separate from main networks. This makes systems safer.
New technologies will improve how networks isolate and secure data. These trends focus on stronger protection and easier management.
Advancements In Security Protocols
Security protocols keep data safe during network use. New protocols will stop more types of cyberattacks. They will also work faster and use less power.
Improved encryption and authentication methods will make guest isolation more reliable. These changes help prevent unauthorized access.
- Stronger encryption standards
- Multi-factor authentication for guests
- Real-time threat detection
Integration With Iot Devices
Internet of Things (IoT) devices are common in homes and offices. Future networks will isolate these devices better to stop attacks.
Guest isolation networks will separate IoT devices from critical systems. This limits damage if a device is hacked.
- Separate networks for IoT and guests
- Automatic device recognition
- Secure communication channels
Automation And Ai In Network Management
Automation and artificial intelligence will make managing guest isolation easier. They can detect problems and fix them fast.
AI will learn normal network behavior. It will block unusual activity without human help. Automation will reduce errors and save time.
- AI-based threat detection
- Automatic network configuration
- Real-time monitoring and alerts
Frequently Asked Questions
What Is A Guest Isolation Network?
A guest isolation network is a security feature used in virtualized environments. It separates guest virtual machines from each other and the host system. This ensures that if one VM is compromised, others remain unaffected. This network enhances security by minimizing the risk of unauthorized access.
How Does Guest Isolation Improve Security?
Guest isolation enhances security by segregating virtual machines within a network. It prevents one compromised VM from affecting others. This separation reduces the risk of malware spreading and unauthorized data access. Isolation is crucial for maintaining a secure and stable virtualized environment.
Why Use Guest Isolation Networks In Virtual Environments?
Guest isolation networks are crucial for maintaining security in virtual environments. They prevent unauthorized access between virtual machines. Isolation ensures that one compromised machine doesn’t impact others. This makes it easier to manage security and compliance, and reduces the risk of data breaches.
Can Guest Isolation Affect Network Performance?
Guest isolation can impact network performance, but it’s generally minimal. The security benefits outweigh potential performance issues. Properly configured, it ensures efficient operation without significant delays. Regular monitoring and optimization can mitigate any performance concerns, ensuring a balance between security and network speed.
Conclusion
Guest isolation networks protect devices by keeping them separate. They reduce risks from unknown or unsafe connections. Setting up these networks is simple and effective. Small businesses and homes benefit from better security. Use guest networks to keep your main system safe.
This approach stops threats from spreading inside your network. Remember, safety starts with smart network choices. Try guest isolation to control access and protect data. It makes your internet use safer and more reliable.
16 min read